
The digital age has empowered small businesses to flourish, but it has also exposed them to a growing landscape of cyber threats. A 2023 report by the Small Business Administration (SBA) revealed that a staggering 60% of small businesses experienced a cyberattack in the past year, highlighting the vulnerability of these organizations. These attacks can have devastating consequences, causing financial losses, operational disruptions, and reputational damage.
Even if a small business believes it lacks valuable data, it remains a target. Cybercriminals may seek access to customer information, intellectual property, or simply leverage compromised systems for further attacks. For instance, a recent attack on a small accounting firm resulted in the exposure of sensitive tax information for hundreds of clients, demonstrating the potential impact of a breach.
Proactive measures are crucial to mitigate these risks. A security gap analysis serves as a vital tool in this fight. It systematically identifies vulnerabilities in a small business’s cybersecurity posture, allowing them to prioritize risks and implement targeted security controls. By proactively addressing these gaps, small businesses can significantly enhance their defenses and build resilience against ever-evolving cyber threats.
Understanding Your Security Landscape
Building a Strong Foundation
Before embarking on a security gap analysis, it’s crucial to gain a comprehensive understanding of your organization’s security landscape. This foundational knowledge serves as a roadmap, guiding you in identifying vulnerabilities and prioritizing risks.
Critical Assets: The Cornerstones of Your Business
Imagine your business as a complex ecosystem. Critical assets your data, systems, and infrastructure represent the cornerstones upon which this ecosystem thrives. These assets are vital for day-to-day operations, customer interactions, and overall business continuity. A data breach compromising customer records, for example, could erode trust and lead to financial penalties. Similarly, compromised financial data could disrupt payroll or vendor payments, causing significant operational hurdles.
Data in Focus: Understanding What You Have

The data your business stores and processes is another critical asset. This can encompass a wide spectrum, including customer data (names, addresses, payment information), financial data (bank account details, transaction records), and intellectual property (trade secrets, proprietary research).
Data Classification: Prioritizing Protection
Not all data is created equal. Data classification helps categorize data based on its sensitivity. Highly confidential information like customer credit card numbers or trade secrets naturally requires stricter security controls compared to publicly available marketing materials. This classification system plays a vital role in tailoring your security measures to effectively safeguard your most valuable assets.
Existing Security Controls: Taking Stock of Your Defenses
Finally, it’s essential to take stock of your current security controls. These are the safeguards you have already implemented to protect your critical assets. Common security controls include firewalls (filtering incoming and outgoing network traffic), access controls (restricting user access to sensitive data and systems), and antivirus software (detecting and preventing malware infections). Identifying existing controls is the first step towards evaluating their effectiveness in addressing potential security gaps.
By thoroughly understanding your critical assets, data, and current security posture, you lay the groundwork for a successful security gap analysis. This knowledge empowers you to identify weaknesses, prioritize risks, and ultimately, build a more robust cybersecurity defense for your small business.
Conducting a Security Gap Analysis
| Technique | Description |
|---|---|
| Self-Assessment | Internal evaluation of security controls and procedures against industry best practices or established frameworks. |
| Vulnerability Scans | Automated scans that identify weaknesses in systems and applications. |
| Penetration Testing | Simulated cyberattacks to identify exploitable vulnerabilities. |
| Security Audits | Comprehensive reviews of an organization's security posture conducted by independent security professionals. |
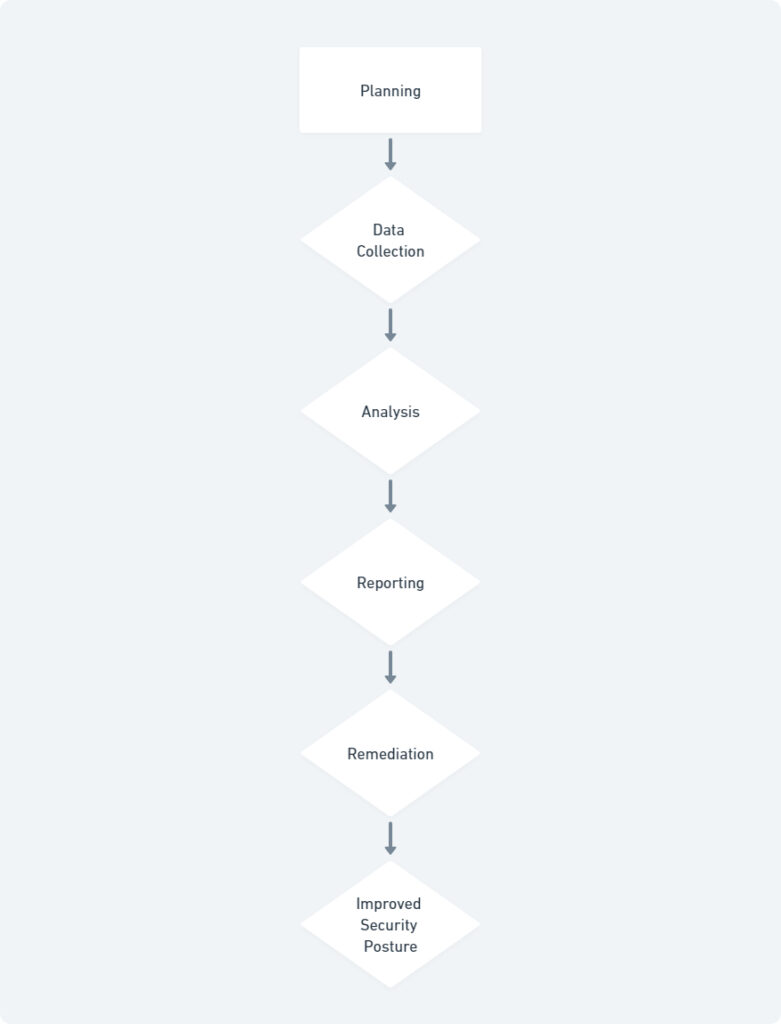
- A – Planning: This stage involves defining the scope and objectives of the security gap analysis. It also includes selecting the appropriate techniques and assigning roles and responsibilities.
- B – Data Collection: This stage involves gathering information about the organization’s security posture, including its assets, systems, applications, security controls, and policies.
- C – Analysis: The collected data is analyzed to identify vulnerabilities, assess risks, and prioritize security gaps.
- D – Reporting: The findings of the analysis are documented in a comprehensive report. This report should outline the identified gaps, their severity, and recommendations for remediation.
- E – Remediation: A remediation plan is developed to address the identified security gaps. This plan should include specific actions, timelines, and resource allocation for implementing necessary controls.
- F – Improved Security Posture: By implementing the remediation plan, the organization strengthens its overall security posture and reduces its cyber risk.
A thorough security gap analysis acts as a roadmap for identifying and addressing vulnerabilities in your organization’s cybersecurity defenses. Selecting the appropriate technique hinges on a critical evaluation of your business needs and resource constraints.

- Self-assessments (security gap analysis), often facilitated by questionnaires or checklists, offer a cost-effective way for small businesses to gain an initial understanding of their security posture. While readily available online or from industry associations, they may lack the depth of more advanced techniques.
- Vulnerability scans (cybersecurity assessment), automated tools that identify weaknesses in systems and applications, provide valuable insights with minimal disruption. However, they may miss certain vulnerabilities and require skilled personnel to interpret the results.
- Penetration testing (penetration testing), which simulates real-world cyberattacks, offers a more in-depth analysis by actively exploiting vulnerabilities. This technique can be highly effective but can also be disruptive and resource-intensive for smaller businesses.
- Security audits (cybersecurity risk assessment), comprehensive reviews conducted by external security professionals, provide the most thorough assessment but are often the most expensive option.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework offers a valuable resource for selecting appropriate security gap analysis techniques based on your business context.
For small businesses, starting with self-assessments and vulnerability scans can be a practical first step. However, for more complex environments or industries with strict compliance requirements, engaging external security professionals for penetration testing or security audits might be necessary. Regardless of the chosen technique, a successful security gap analysis requires a systematic approach, beginning with thorough planning and data collection, followed by meticulous analysis, comprehensive reporting, and ultimately, the implementation of a remediation plan to address identified security gaps.
Prioritizing Security Risks

A security gap analysis uncovers a multitude of vulnerabilities, but not all pose equal threats. Effective risk management hinges on prioritizing these vulnerabilities based on their potential impact and likelihood of exploit. A high-impact vulnerability, such as a flaw that could lead to a complete data breach, requires immediate attention compared to a low-impact one that might only affect a non-critical system. Likewise, a vulnerability with a high likelihood of exploit, perhaps due to publicly known weaknesses, demands swifter remediation than one requiring a complex and targeted attack.
Standardized risk assessment frameworks, such as the Common Vulnerability Scoring System (CVSS), offer a structured approach to prioritizing vulnerabilities. CVSS assigns a score based on exploitability, severity, and scope, enabling an objective comparison of various threats.
However, prioritization is not a purely technical exercise. Business context plays a crucial role. For instance, a healthcare provider might prioritize vulnerabilities related to patient data security more than a retail store, even if the technical severity might be similar. Industry regulations can also dictate how certain vulnerabilities are prioritized.
By carefully considering both the technical severity and the specific business context, small businesses can allocate limited resources effectively and address the most pressing security risks first. This ensures they proactively mitigate cyber threats and safeguard their critical assets.
Developing a Remediation Plan

The culmination of a security gap analysis is the development of a remediation plan, a crucial roadmap for addressing the identified security gaps. This plan outlines the specific actions required to mitigate identified vulnerabilities and strengthen your overall cybersecurity posture.
A comprehensive remediation plan should encompass several key elements:
- Specific Actions: For each identified vulnerability, the plan should detail the specific actions required to address it. This could involve patching software with the latest security updates, implementing stricter access controls, or upgrading outdated hardware.
- Timelines: Establishing clear deadlines for completing remediation activities is essential. Assigning realistic timelines ensures a timely response and minimizes the window of opportunity for cyberattacks.
- Resource Allocation: Effective remediation requires allocating the necessary resources, including personnel, budget, and tools. This may involve training existing staff, hiring additional security professionals, or acquiring new security software.
The plan should not be a one-time effort. Ongoing monitoring and maintenance are critical to ensure the effectiveness of implemented controls. Regularly scheduled vulnerability scans and security assessments can identify new threats and ensure existing controls remain functional. Additionally, employee security awareness training plays a vital role in mitigating human error, a significant factor in many cyberattacks.
By following a well-defined remediation plan, you can systematically address security gaps, significantly reducing your organization’s cyber risk profile. Remember, cybersecurity is an ongoing process, and continuous vigilance is essential to stay ahead of evolving threats.
The ever-present threat landscape underscores the critical need for cybersecurity for small businesses. A successful security strategy hinges on a thorough understanding of your critical assets, data, and existing security controls. This article has equipped you with the knowledge to conduct a security gap analysis, a systematic process for identifying and prioritizing vulnerabilities in your cybersecurity defenses.
By following the steps outlined, you can gain valuable insights into your organization’s security posture. This empowers you to develop a targeted remediation plan that addresses the vulnerabilities posing the most significant risk. It is crucial to recognize that cybersecurity is a continuous process, not a one-time achievement. Regular security gap analyses and continuous monitoring are essential for maintaining a robust defense against cyber threats.
For additional resources to bolster your cybersecurity efforts, explore the Small Business Administration (SBA) page on cybersecurity for small businesses . This resource provides valuable guidance and best practices to help small businesses of all sizes navigate the complex world of cybersecurity.
By taking a proactive approach and leveraging available resources, small businesses can significantly mitigate cyber risks and safeguard their critical assets, ensuring long-term success in today’s digital age.
By taking a proactive approach and leveraging available resources, small businesses can significantly mitigate cyber risks and safeguard their critical assets, ensuring long-term success in today’s digital age. In addition to the guidance provided in this article, for a deeper exploration of how cybersecurity can be leveraged to enhance your small business’s protection, explore our comprehensive guide: How Small Businesses Can Leverage Cybersecurity for Enhanced Protection. This resource dives into the specific benefits of a cybersecurity strategy and outlines a step-by-step approach to building a robust defense against cyberattacks.
Categorized in:
Comments