
The digital age has empowered small businesses to flourish, but it has also introduced a relentless undercurrent of cyber threats. In 2023, a study by Accenture revealed that 43% of cyberattacks targeted small businesses, highlighting their increasing vulnerability. These attacks can be devastating, causing financial losses exceeding $2.4 million on average, according to a report by The Global Impact of Business Email Compromise 2023.
Protecting sensitive customer data, such as financial records and personal information, is paramount for small businesses. Data breaches can erode consumer trust, potentially leading to customer churn and reputational damage. Furthermore, the regulatory landscape is constantly evolving, with stricter cybersecurity compliance requirements being implemented across various industries. Non-compliance can result in hefty fines, legal repercussions, and operational disruptions, jeopardizing a small business’s future. In this ever-changing environment, prioritizing cybersecurity compliance is no longer optional it’s a critical business imperative.
Importance of Cybersecurity for Small Businesses

For small businesses, a successful cyberattack can be an existential threat. A 2023 report by the Ponemon Institute found that the average cost of a data breach for a small business is a staggering $4.24 million. These financial losses can cripple a small business, impacting everything from operational costs to future investments. Beyond the immediate financial blow, cyberattacks can inflict severe reputational damage. When customer data is compromised, trust evaporates quickly. A study by IBM revealed that 87% of customers would take their business elsewhere after a data breach, highlighting the devastating impact on customer loyalty.
The very lifeblood of a small business – its sensitive data – is a prime target for cybercriminals. Customer information, including financial records, personally identifiable information (PII), and intellectual property are all valuable assets that require robust protection. A successful cyberattack can lead to the exposure of this sensitive data, putting customers at risk of identity theft and fraud.
The landscape of cyber threats is constantly evolving, but some tactics remain prevalent. Phishing attacks, where malicious actors attempt to trick employees into revealing sensitive information or clicking on infected links, are a common method for gaining unauthorized access to systems. Malware, malicious software designed to disrupt operations or steal data, can be downloaded unknowingly through seemingly legitimate websites or email attachments.
Ransomware, a particularly disruptive form of malware, encrypts a victim’s data, rendering it inaccessible until a ransom is paid. These threats are not theoretical; a 2022 Verizon Business Insider Threat Report found that 82% of cyberattacks involved a human element, highlighting the importance of employee awareness and training in cybersecurity best practices.
By prioritizing cybersecurity, small businesses can safeguard their financial stability, protect their customers, and build a foundation for sustainable growth.
Understanding Cybersecurity Regulations

Cybersecurity regulations serve as the cornerstone of data security standards in today’s digital landscape. These regulations establish a framework for organizations to manage and protect sensitive data. They outline specific requirements for data security controls, breach notification procedures, and employee training. By adhering to these regulations, businesses demonstrate their commitment to safeguarding customer information and building trust.
The specific regulations that apply to a small business depend heavily on the type of data it collects and stores. Here’s a breakdown of some key regulations and the industries they impact:
| Regulation | Focus Area | Relevant Industries |
|---|---|---|
| Health Insurance Portability and Accountability Act (HIPAA) | Protects patient health information | Healthcare providers, health plans, healthcare clearinghouses |
| Payment Card Industry Data Security Standard (PCI DSS) | Protects credit card information | Businesses that accept, transmit, or store credit card data |
| Gramm-Leach-Bliley Act (GLBA) | Protects financial information | Financial institutions, lenders, credit reporting agencies |
| Federal Trade Commission (FTC) Safeguards Rule | Protects customer information | Businesses that collect and maintain customer data |
Non compliance with these regulations can have significant consequences for small businesses. Regulatory bodies may impose hefty fines, ranging from tens of thousands to millions of dollars depending on the severity of the violation. Additionally, legal repercussions such as lawsuits from affected individuals or businesses can further strain a small business’s resources. The damage to a company’s reputation can also be substantial, leading to a loss of customer trust and a decline in market share.
Beyond the immediate consequences, non-compliance exposes a business to a heightened risk of cyberattacks. By demonstrating a lax approach to data security, a business becomes a more attractive target for malicious actors. Therefore, prioritizing cybersecurity compliance is not just a legal obligation, but a strategic imperative for safeguarding a small business’s future.
Building a Cybersecurity Compliance Plan
A robust cybersecurity compliance plan serves as the roadmap for a small business to navigate the ever-evolving landscape of data security regulations. This plan outlines the essential steps required to achieve and maintain compliance, ultimately safeguarding sensitive data and building customer trust.
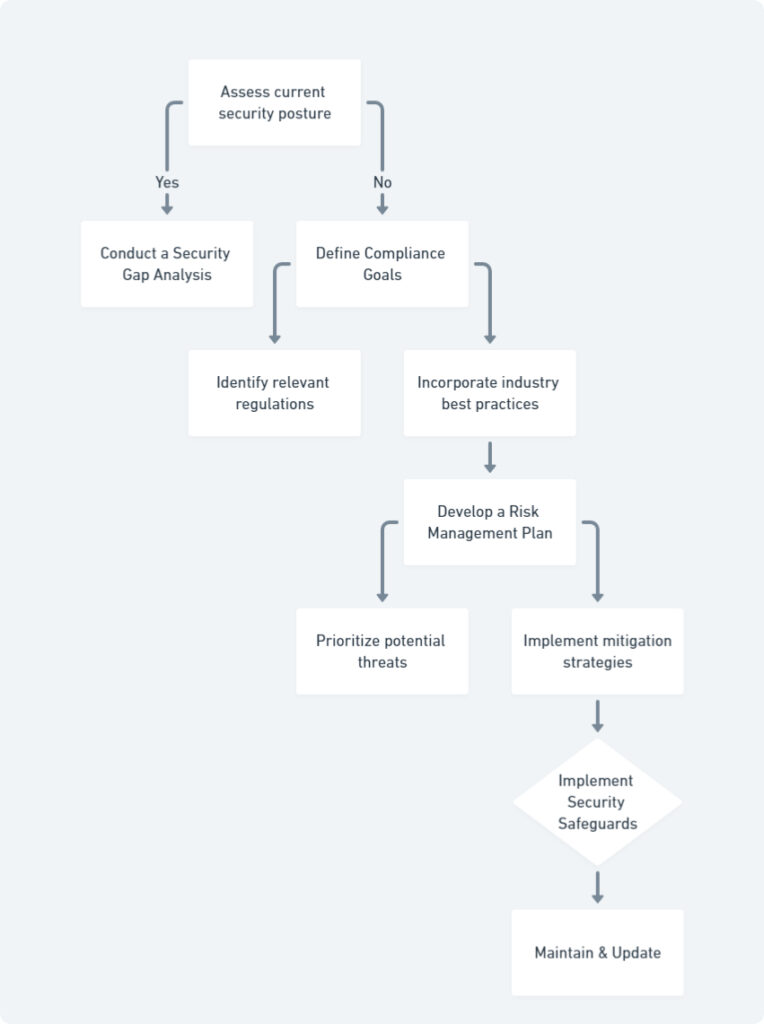
Building a Cybersecurity Compliance Plan: A Step-by-Step Guide
The first crucial step involves conducting a thorough security gap analysis. This analysis, which can be facilitated by free or low-cost tools from some cybersecurity vendors, identifies weaknesses in your network infrastructure and systems. By understanding your vulnerabilities, you can prioritize which areas require the most attention.
Once you have a clear picture of your current security posture, the next step is to define your compliance goals. This involves pinpointing the specific regulations that apply to your business based on the type of data you collect and store. Researching industry best practices for data security will further strengthen your compliance framework.
With your goals established, it’s essential to develop a comprehensive risk management plan. Prioritize potential cybersecurity threats based on their likelihood and potential impact on your business. This could involve threats like phishing attacks, malware infections, or ransomware attacks. Once you’ve identified the most significant threats, implement mitigation strategies to minimize their impact. This might include employee training programs, robust password policies, or investing in firewalls and intrusion detection systems.
Involving Key Stakeholders
Building a successful cybersecurity compliance plan requires a collaborative effort. Actively involve key stakeholders from different departments, including management and IT personnel. Management’s commitment to cybersecurity is essential for allocating resources and ensuring company-wide adoption of security protocols. IT personnel’s expertise will be invaluable in implementing and maintaining the technical aspects of the compliance plan. By fostering collaboration and open communication, small businesses can significantly enhance their cybersecurity posture.
Implementing Cybersecurity Safeguards

Achieving and maintaining cybersecurity compliance necessitates implementing a multifaceted approach that safeguards sensitive data across various access points. Here, we explore essential security measures small businesses can leverage:
Access Controls:
- User Access Management: Establish a system that grants access to data and systems on a “need-to-know” basis. Implement multi-factor authentication (MFA) to add an extra layer of security during login attempts.
- Data Encryption: Encrypt sensitive data both at rest and in transit. This renders the data unreadable even if intercepted by unauthorized individuals.
- Strong Password Policies: Enforce robust password creation policies that mandate a minimum password length, character complexity (including uppercase, lowercase, numbers, and symbols), and regular password changes.
Network Security:
- Firewalls: Firewalls act as a barrier between your internal network and the external world, filtering incoming and outgoing traffic based on predefined security rules.
- Intrusion Detection Systems (IDS): These systems continuously monitor network activity for suspicious behavior that might indicate a cyberattack.
- Secure Wi-Fi Configuration: Utilize strong encryption protocols (WPA2 or WPA3) to secure your Wi-Fi network and prevent unauthorized access. Additionally, disable guest Wi-Fi when not in use and implement separate networks for business and personal devices.
Data Security:
- Data Backup and Recovery Procedures: Regularly back up your critical data to a secure offsite location. This ensures data recovery in case of a cyberattack, hardware failure, or natural disaster.
- Employee Training on Data Handling: Educate employees on proper data handling practices, including identifying phishing attempts, avoiding suspicious email attachments, and adhering to company data security policies. Resources like the National Institute of Standards and Technology (NIST) Cybersecurity Framework provide valuable training materials.
Financial Assistance and Ongoing Maintenance
Several government initiatives and non-profit organizations offer free or affordable cybersecurity solutions specifically tailored for small businesses. Exploring these resources can significantly bolster your cybersecurity posture without breaking the bank.
Finally, staying updated with the latest security patches and software updates is paramount. Cybercriminals constantly seek out vulnerabilities in outdated software, making it crucial to install updates as soon as they become available. By implementing these security measures and fostering a culture of cybersecurity awareness within your organization, small businesses can significantly enhance their data security and achieve regulatory compliance.
Ongoing Compliance and Risk Management

The cybersecurity landscape is constantly evolving, demanding a continuous commitment to improvement. Just achieving compliance isn’t enough; ongoing monitoring and proactive risk management are essential for long-term success.
Regular security assessments, including vulnerability scans and penetration testing, should be conducted to identify and address potential weaknesses in your defenses. Vulnerability scans systematically search for known security flaws in your systems and software, allowing for timely patching. Penetration testing simulates a cyberattack, mimicking the tactics of real-world hackers to identify exploitable vulnerabilities.
Investing in employee training programs is equally important. By educating employees on the latest cybersecurity threats and best practices, you empower them to become the first line of defense against cyberattacks. Training should cover topics such as phishing awareness, password security, and proper data handling procedures.
Furthermore, every small business should develop a comprehensive incident response plan. This plan outlines the steps to be taken in the event of a data breach, including data containment, notification of affected individuals, and remediation efforts. Having a well-defined plan minimizes confusion and ensures a swift and efficient response to a potential cyber incident.
By adopting a continuous improvement mindset and implementing these ongoing security measures, small businesses can stay ahead of evolving threats and ensure long-term compliance with cybersecurity regulations.
In today’s digital age, cybersecurity compliance is no longer an option for small businesses; it’s a necessity. By prioritizing compliance, small businesses safeguard sensitive customer data, a critical asset in today’s competitive landscape. Compliance fosters trust with customers, leading to stronger brand loyalty and potentially attracting new business. Furthermore, a robust cybersecurity posture demonstrates a commitment to responsible data management, potentially giving a small business a competitive edge. Resources such as the Small Business Administration’s cybersecurity guidance offer valuable information to help small businesses navigate the complex world of cybersecurity compliance. By taking a proactive approach, small businesses can build a secure foundation for sustainable growth and success.
By prioritizing compliance and implementing robust security measures, small businesses can navigate the digital age with confidence. This article has equipped you with the foundational knowledge to achieve compliance. To bolster your defenses and gain insights into the top cyber threats targeting small businesses, refer to our comprehensive analysis in “Top Cybersecurity Threats Facing Small Businesses Today”
Categorized in:
Comments