
Cloud & AI: A Robust Shield Against Modern Cyber Threats
Cybersecurity, the practice of safeguarding digital assets from unauthorized access, use, disclosure, disruption, modification, or destruction, is paramount for contemporary businesses. In an era characterized by rapid digital transformation, organizations of all sizes are increasingly reliant on technology to operate efficiently. Concurrently, the threat landscape has evolved into a complex and dynamic environment, with cybercriminals employing sophisticated tactics to exploit vulnerabilities. From data breaches compromising sensitive information to ransomware attacks crippling operations, the potential consequences of cyber incidents are severe. To effectively mitigate these risks, businesses must adopt a proactive and comprehensive approach to cybersecurity. The integration of cloud computing and artificial intelligence (AI) technologies offers a promising avenue for bolstering defenses and achieving a higher level of security. By strategically leveraging cloud and AI solutions, organizations can significantly enhance their ability to detect, prevent, and respond to cyber threats, thereby safeguarding their digital assets and ensuring business continuity.
Understanding the Cybersecurity Landscape in the UAE

The United Arab Emirates (UAE) has embarked on an ambitious digital transformation journey, fostering a burgeoning digital economy. While this economic growth presents significant opportunities, it also introduces a complex cybersecurity landscape. The increasing reliance on technology across various sectors, from finance and healthcare to government and energy, has elevated the potential risks associated with cyberattacks. To address these challenges, the UAE government has established the UAE Cyber Security Council to oversee the nation’s cybersecurity strategy and ensure compliance with stringent regulations. Safeguarding critical infrastructure and protecting sensitive data has become paramount, necessitating robust cybersecurity solutions that can withstand the evolving threat landscape.
The Role of Cloud Computing in Cybersecurity

Cloud computing represents a transformative paradigm in IT infrastructure, delivering computing services including servers, storage, databases, networking, software, analytics, and intelligence over the internet. This model empowers organizations to access and utilize resources on-demand, eliminating the complexities and costs associated with managing on-premises IT infrastructure. By adopting cloud computing, businesses can focus on core competencies while reaping the benefits of scalability, cost-efficiency, and agility.
In the realm of cybersecurity, cloud-based solutions offer a robust defense against evolving threats. Cloud security services provide a comprehensive suite of protection measures, including data encryption, access controls, threat detection, and incident response. These solutions often leverage advanced technologies and expertise, enabling organizations to enhance their security posture without the need for significant in-house investments.
Cloud computing encompasses several deployment models, each with distinct security implications. Infrastructure as a Service (IaaS) provides the most fundamental level, offering virtualized computing resources. Platform as a Service (PaaS) delivers a development platform for building and deploying applications. Software as a Service (SaaS) provides applications via the internet. While the cloud offers numerous advantages, organizations must address potential security challenges, such as data privacy breaches, unauthorized access, and service disruptions. Implementing robust security measures, including regular security assessments, employee training, and incident response plans, is crucial to mitigating these risks and safeguarding sensitive information in the cloud environment.
By strategically integrating cloud computing and cybersecurity, businesses can significantly strengthen their overall security posture, mitigate risks, and protect valuable assets.
The Power of AI in Cybersecurity

Artificial Intelligence (AI), the simulation of human intelligence in machines, has emerged as a transformative force across industries, including cybersecurity. By leveraging advanced algorithms and machine learning, AI systems can analyze vast datasets, identify patterns, and make informed decisions at unprecedented speeds. This capability is invaluable in combating the ever-evolving cyber threat landscape.
AI excels in threat detection and prevention by continuously monitoring networks and systems for anomalies indicative of malicious activity. Machine learning algorithms can rapidly analyze large volumes of data to identify and classify cyber threats, such as malware, phishing attacks, and ransomware. This proactive approach empowers organizations to detect and neutralize threats before they can cause significant damage.
Beyond threat detection, AI plays a pivotal role in incident response and remediation. When a security breach occurs, AI-powered systems can rapidly analyze incident data to determine the scope and impact of the attack. By automating routine tasks, such as vulnerability assessment and patch management, AI frees up security teams to focus on critical incident response activities. Furthermore, AI can provide valuable insights into the attacker’s tactics, techniques, and procedures, aiding in the development of effective countermeasures.
While AI offers immense potential for enhancing cybersecurity, it is essential to consider ethical implications. AI systems must be developed and deployed responsibly to prevent unintended consequences. Bias in training data can lead to discriminatory outcomes, and the potential for misuse of AI technology poses significant risks. Organizations must establish robust ethical frameworks and governance structures to ensure that AI is used ethically and beneficially.
By harnessing the power of AI while adhering to ethical principles, organizations can significantly strengthen their cybersecurity posture and protect against emerging threats.
Leveraging Cloud and AI for Comprehensive Cybersecurity
The convergence of cloud computing and artificial intelligence (AI) presents a formidable alliance in the realm of cybersecurity. By synergistically combining these technologies, organizations can achieve a level of protection previously unattainable through traditional security measures.
AI-powered cloud security solutions offer a proactive and adaptive approach to mitigating cyber risks. Machine learning algorithms, embedded within cloud platforms, can analyze vast volumes of data to identify patterns indicative of malicious activity. These solutions excel at detecting advanced persistent threats (APTs), zero-day vulnerabilities, and insider threats, which often evade traditional security measures. Furthermore, AI-driven threat intelligence capabilities enable organizations to stay informed about the latest attack vectors and develop countermeasures accordingly.
Real-world examples underscore the efficacy of cloud and AI in safeguarding digital assets. For instance, financial institutions have successfully employed AI-powered cloud platforms to detect and prevent fraudulent transactions in real-time, resulting in significant cost savings and improved customer satisfaction. Additionally, healthcare providers have leveraged AI to secure patient data stored in the cloud, mitigating the risk of data breaches and ensuring compliance with stringent regulations.
A holistic approach to cybersecurity is essential for achieving optimal protection. While cloud and AI offer powerful capabilities, they should be integrated into a comprehensive security framework that encompasses people, processes, and technology. This framework should include robust access controls, employee security awareness training, incident response planning, and regular security assessments.
By adopting a holistic perspective and strategically leveraging cloud and AI technologies, organizations can build a resilient cybersecurity posture capable of withstanding the evolving threat landscape.
Comparison of Traditional Security vs. Cloud and AI-Based Security
| Feature | Traditional Security | Cloud and AI-Based Security |
|---|---|---|
| Deployment | On-premises infrastructure | Cloud-based infrastructure |
| Scalability | Limited scalability | Highly scalable |
| Cost | High upfront costs | Lower upfront costs, pay-per-use |
| Threat Detection | Primarily signature-based | Behavior-based, anomaly detection |
| Response Time | Slow response to threats | Real-time threat detection and response |
| Automation | Limited automation | Extensive automation |
By understanding the key differences between traditional and cloud-based security approaches, organizations can make informed decisions about their cybersecurity strategy.
Building a Strong Cybersecurity Foundation

A robust security infrastructure is the cornerstone of effective cybersecurity. It serves as the bedrock upon which additional layers of protection can be built. To establish a strong foundation, organizations must prioritize a comprehensive risk assessment and vulnerability management program. By identifying potential threats and weaknesses, businesses can allocate resources efficiently to mitigate risks and protect critical assets.
Employee awareness and training are indispensable components of a robust cybersecurity strategy. Educating employees about common cyber threats, such as phishing and social engineering, empowers them to act as the first line of defense. By fostering a culture of cybersecurity awareness, organizations can significantly reduce the risk of human error-related breaches.
Moreover, developing a comprehensive incident response plan is crucial for minimizing the impact of cyberattacks. A well-structured plan outlines the steps to be taken in the event of a security breach, from detection and containment to recovery and lessons learned. By having a clear and actionable plan in place, organizations can respond effectively to incidents, limiting damage and preserving business continuity.
In conclusion, a strong cybersecurity foundation is built upon a combination of robust infrastructure, thorough risk assessment, employee training, and a well-defined incident response plan. By investing in these essential elements, organizations can significantly enhance their resilience against cyber threats.
While building a strong cybersecurity foundation requires significant investment, there are strategies to optimize resource allocation without compromising security. For a deeper dive into cost-effective cybersecurity measures, refer to our article: “Cost Effective Cybersecurity: Balancing Budget and Security Needs.“
Choosing the Right Cloud and AI Solutions
Selecting the optimal cloud and AI solutions is a critical step in enhancing an organization’s cybersecurity posture. A meticulous evaluation process is essential to identify vendors that align with specific security requirements and business objectives. Key factors to consider include the vendor’s reputation for delivering reliable and secure services, their compliance with industry standards and regulations, and the overall cost-effectiveness of their solutions.
Data privacy and security should be paramount in the vendor selection process. Organizations must carefully assess how vendors protect sensitive information and adhere to stringent data protection regulations. It is essential to verify the existence of robust data encryption, access controls, and incident response capabilities.
To streamline the decision-making process, a structured evaluation framework can be employed. A decision-making flowchart can visually represent the key criteria and decision points, aiding in the selection of the most suitable cloud and AI solutions. By following a systematic approach and prioritizing data privacy and security, organizations can make informed choices that bolster their cybersecurity defenses.
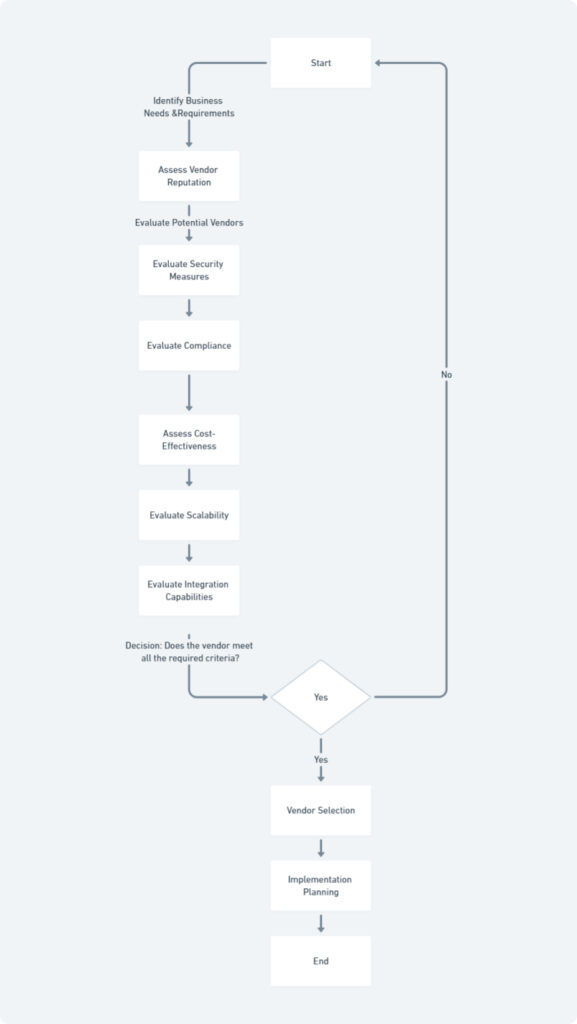
By diligently selecting cloud and AI solutions that meet stringent security standards, organizations can significantly strengthen their cybersecurity posture and mitigate the risk of data breaches.
In an era characterized by rapid digital transformation and escalating cyber threats, the integration of cloud and AI technologies is imperative for bolstering organizational cybersecurity. By leveraging these innovative solutions, businesses can significantly enhance their ability to detect, prevent, and respond to cyberattacks. A proactive and adaptive approach to security is essential to safeguard against the evolving threat landscape. To ensure the protection of valuable assets, organizations must prioritize cybersecurity investments and cultivate a culture of security awareness across all levels of the organization.
Categorized in:
Comments