
Cyber Threat Intelligence for UAE SMEs
Cyber threat intelligence (CTI) has emerged as a critical component of modern cybersecurity strategies, offering businesses the ability to anticipate, identify, and mitigate threats before they cause damage. For small and medium-sized enterprises (SMEs) in the UAE, this proactive approach is vital, as the region continues to experience a sharp rise in cyberattacks targeting businesses of all sizes. In 2023 alone, the UAE saw a 30% increase in cybercrime, with SMEs bearing a significant portion of the attacks . Dark web data has become a crucial element in this intelligence gathering, providing insights into potential breaches, exposed credentials, and hacker activity. As cybercriminals increasingly use the dark web to trade stolen data and coordinate attacks, leveraging this hidden layer of the internet allows businesses to stay one step ahead, ensuring their cybersecurity defenses are robust and up-to-date. For UAE enterprises, implementing dark web intelligence is no longer a luxury but a necessity.
What is Cyber Threat Intelligence?
Cyber Threat Intelligence (CTI) refers to the process of collecting, analyzing, and interpreting data about potential or existing cyber threats. It enables organizations to make informed decisions about their cybersecurity posture by identifying potential risks, such as vulnerabilities and targeted attacks. The goal of CTI is to predict and mitigate threats before they cause harm, providing a proactive defense mechanism. Unlike traditional cybersecurity measures that react to attacks, CTI focuses on anticipating and preventing security incidents, making it a cornerstone of an effective cybersecurity risk assessment.
CTI draws from multiple data sources to deliver a comprehensive view of the threat landscape. These sources include internal network data, which provides insights into anomalies within an organization, information from known threat actors, and dark web intelligence. Dark web data is particularly valuable as it reveals stolen credentials, compromised information, and discussions between malicious actors. Integrating these sources allows businesses to enhance their cybersecurity assessment and identify security gaps that could lead to significant breaches.

The Role of the Dark Web in Cyber Threat Intelligence
The dark web is an elusive and hidden part of the internet, often used by threat actors to exchange sensitive data, sell stolen information, and coordinate cyberattacks. For businesses, the dark web presents both a significant risk and a valuable source of intelligence. By monitoring dark web activities, companies can gain insights into emerging threats, compromised credentials, and black market transactions involving their assets. This intelligence is critical for a comprehensive cybersecurity risk assessment, allowing businesses to stay ahead of attackers.
The types of information commonly found on the dark web include stolen login credentials, personal data, and financial details that are often traded or sold. Hackers also use forums on the dark web to share exploit strategies and discuss vulnerabilities in various systems. By intercepting these discussions and monitoring the sale of company-specific data, businesses can quickly close security gaps and implement preventative measures.
Incorporating dark web data into security gap analysis helps businesses understand where they are vulnerable and what steps they need to take to protect themselves. A 2022 report on dark web intelligence showed that organizations with ongoing dark web monitoring were 60% more likely to prevent attacks before they caused major damage (source). This proactive approach helps businesses minimize risks and respond effectively to potential threats, making dark web intelligence a crucial element in modern cybersecurity strategies.
By leveraging these insights, companies can develop stronger defenses, protect sensitive data, and reduce the risk of costly breaches. For businesses looking to enhance their cybersecurity posture and monitor dark web threats effectively, consider exploring the Dark Web Scan services offered by Cybernod to safeguard your enterprise. Visit Cybernod for more information on how we can help protect your business from hidden cyber threats.
How UAE Enterprises Can Leverage Dark Web Intelligence

To effectively integrate dark web intelligence into their cybersecurity strategies, UAE businesses can follow several practical steps to enhance protection against evolving cyber threats. Leveraging specialized services, conducting regular assessments, and integrating intelligence findings with existing security measures are crucial actions that help identify and mitigate risks.
1. Using Specialized Services to Scan the Dark Web
The first step for any UAE business is to engage with specialized dark web monitoring services. These services utilize sophisticated tools to scan the dark web for company-related information, such as compromised credentials or sensitive data being traded. By partnering with experts in this field, businesses can regularly receive alerts about potential threats and address vulnerabilities before they escalate.
2. Regular Cybersecurity Assessments
Dark web intelligence should be incorporated into a company’s broader cybersecurity assessment framework. Businesses should perform regular security gap analysis to identify potential weak points where data may be exposed or exploited. These assessments not only help address existing risks but also adapt security protocols to match the changing landscape of cyber threat
3. Integrating Dark Web Findings with Other Cybersecurity Measures
Dark web intelligence is most effective when integrated with other cybersecurity services. For instance, companies can combine it with endpoint protection, email filtering, and multi-factor authentication to create a comprehensive defense strategy. This layered approach ensures that vulnerabilities identified from dark web data are addressed holistically, thereby strengthening the overall security posture of the organization.
| Cost Factor | Benefit |
|---|---|
| Service Subscription Fee | Early detection of compromised data |
| Integration with Existing Systems | Reduced risk of major data breaches |
| Ongoing Monitoring | Continuous protection and threat updates |
| Employee Training | Increased awareness and preventative action |
By investing in dark web monitoring and integrating the intelligence into broader security strategies, UAE businesses can better defend against cyber threats. Combining these insights with a regular security gap assessment allows for a proactive approach to cybersecurity, minimizing risks and ensuring that vulnerabilities are swiftly addressed.
Top Cybersecurity Threats for UAE Businesses
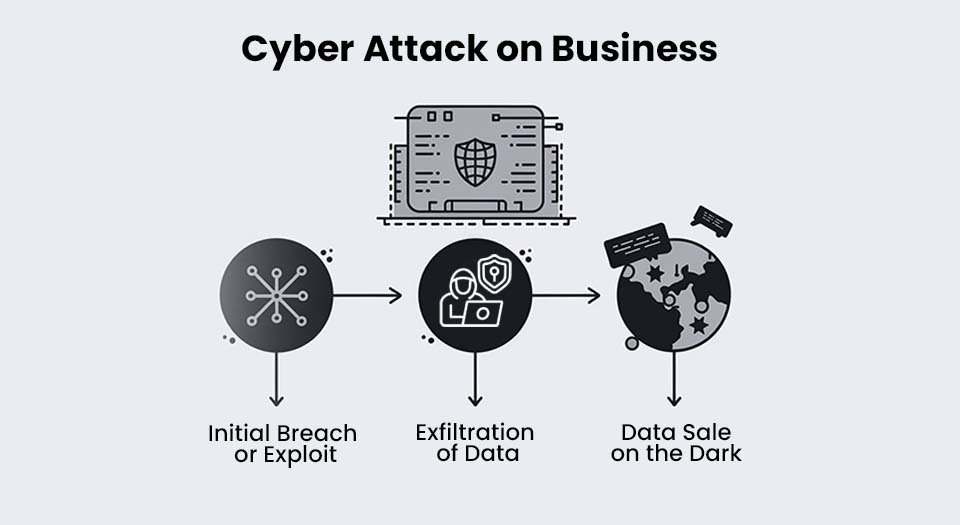
UAE businesses face several significant cybersecurity threats that can cause operational disruption, financial losses, and reputational damage. The most prevalent threats include data breaches, ransomware, and phishing attacks. Each of these threats targets sensitive information and exploits vulnerabilities in systems, making it critical for businesses to adopt robust defenses.
Data breaches are one of the most damaging threats, where attackers gain unauthorized access to confidential data. For small businesses, preventing data breaches is crucial to maintaining customer trust and regulatory compliance. Ransomware is another growing concern, where attackers lock down critical systems and demand payment for their release. This can paralyze business operations for extended periods. Lastly, phishing attacks—where attackers deceive employees into revealing sensitive information—are particularly dangerous for small and medium-sized businesses that may lack advanced cybersecurity training.
Dark web intelligence can play a vital role in mitigating these threats. By actively monitoring dark web forums and marketplaces, businesses can detect compromised credentials, stolen data, and early signs of planned attacks. This intelligence allows companies to take preemptive measures, such as resetting compromised passwords or enhancing security protocols, significantly reducing the risk of these cyber threats.
For more comprehensive solutions, businesses can explore Cybernod’s services to prevent data breaches and strengthen their overall security posture.
Benefits of Dark Web Monitoring for Small Enterprises
Dark web monitoring offers significant advantages for small and medium-sized enterprises (SMEs) in the UAE, helping them protect against emerging threats while ensuring compliance with regulatory frameworks. For businesses looking to implement the best cybersecurity solutions, dark web monitoring provides a cost-effective way to detect threats early, preventing data breaches and reducing the financial burden of cyberattacks.
One of the key benefits of dark web monitoring is its alignment with UAE cybersecurity regulations. Frameworks like the National Electronic Security Authority (NESA) mandate strict cybersecurity measures for businesses, requiring continuous threat monitoring and data protection. By implementing dark web monitoring, SMEs can more easily comply with cybersecurity regulations, ensuring that exposed credentials or leaked data are swiftly identified and addressed, helping avoid fines and penalties.
Dark web monitoring also integrates smoothly with cybersecurity services for small businesses, making it a scalable solution that grows as the business expands. By detecting vulnerabilities before they are exploited, SMEs can strengthen their overall cybersecurity posture while staying compliant with UAE laws.
For UAE SMEs seeking the best cybersecurity solutions, dark web monitoring is not just a luxury—it’s a necessity. It ensures regulatory compliance, enhances customer trust, and provides a cost-effective way to protect valuable business data.
Future-Proofing Cybersecurity with Dark Web Intelligence
Incorporating dark web intelligence into broader cybersecurity strategies is essential for any business looking to stay ahead of cyber threats. By proactively monitoring dark web activities, businesses can detect compromised data early and address vulnerabilities before they are exploited. Integrating dark web intelligence into cybersecurity assessments provides a clearer view of potential risks, allowing companies to take decisive actions that reduce exposure to attacks.
For small businesses, choosing the best cybersecurity solution is crucial for both security and compliance. Dark web monitoring not only enhances protection but also helps ensure regulatory requirements are met. Implementing these solutions provides a solid foundation for long-term cybersecurity resilience.
Now is the time for businesses to take immediate steps toward adopting dark web intelligence solutions. Regular cybersecurity assessments and continuous monitoring are vital to safeguarding sensitive information. To ensure your company is protected, explore Cybernod’s services and secure your business against evolving threats.
Want to learn more about protecting your business identity on the dark web?** Check out our article, “Protecting Your Business Identity: The Importance of Dark Web Monitoring in the UAE” for expert insights and practical advice.
Categorized in:
Comments