
The Growing Threat of Phishing for UAE Businesses
Phishing has evolved from simple, deceptive emails into highly sophisticated, targeted attacks that pose significant risks to businesses. According to a 2023 report, phishing attacks increased by 30% globally, with the UAE being a key target due to its rapidly expanding digital economy. These attacks often use social engineering techniques to exploit vulnerabilities in businesses, stealing sensitive data or compromising financial systems.
A critical factor driving the rise of phishing is the dark web, a hidden layer of the internet where cybercriminals trade stolen data, phishing kits, and malware. This underground network provides easy access to tools that enable even unskilled attackers to launch complex campaigns against businesses of all sizes.
For UAE businesses, particularly small and medium-sized enterprises (SMEs), this trend represents an urgent threat. Without adequate cybersecurity measures in place, such as dark web monitoring and phishing prevention strategies, companies risk severe financial and reputational damage. The need for a proactive cybersecurity approach has never been more pressing.
From Basic Scams to Dark Web-Fueled Threats
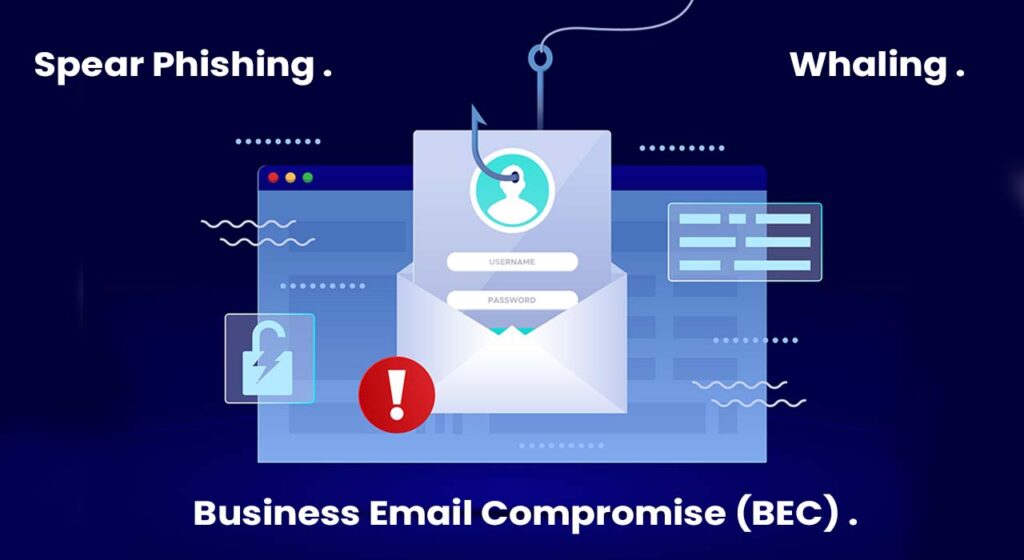
Phishing has come a long way from its early days as a basic email scam designed to trick recipients into revealing personal information. Initially, these attacks relied on mass email campaigns, hoping to catch a few unsuspecting victims with poorly crafted messages. Over time, phishing evolved into more sophisticated forms like spear phishing, where attackers target specific individuals using personalized details, and whaling, which focuses on high-ranking executives to gain access to sensitive corporate information. Another dangerous variant, Business Email Compromise (BEC), has become a major threat, with attackers impersonating trusted sources to steal vast sums of money from businesses.
The dark web plays a critical role in this evolution. This hidden part of the internet allows cybercriminals to trade stolen data, share phishing kits, and sell hacking tools, making it easy for even low-skill attackers to launch complex phishing campaigns. Phishing kits, complete with customizable email templates and instructions, can be purchased for as little as a few dollars, lowering the entry barrier for cybercrime. More concerning is the fact that dark web forums facilitate the sale of stolen credentials, enabling attackers to bypass security protocols and compromise entire systems.
Recent phishing attacks targeting UAE businesses demonstrate the alarming scale and sophistication of these threats. For instance, in 2022, several SMEs in the UAE were targeted by ransomware attacks that began with phishing emails containing malicious links. Once clicked, these links led to the encryption of company data, with the attackers demanding payment for its release. In other cases, credential theft through phishing emails allowed cybercriminals to access sensitive information, posing serious operational and financial risks. Social engineering tactics, where attackers manipulate employees into providing access to corporate systems, have also become a popular method for launching ransomware and data breaches.
Given the increasing sophistication of phishing threats, UAE businesses—especially small and medium-sized enterprises—must adopt comprehensive cybersecurity strategies. Regular cybersecurity risk assessments and proactive cybersecurity assessments are crucial for identifying vulnerabilities and strengthening defenses. Without these measures, businesses are vulnerable to one of the top cybersecurity threats for small businesses today: phishing.
Need help protecting your small business from data breaches? Check out our article, “Practical Steps to Prevent Data Breaches in Small Businesses,” for expert advice and actionable tips.
The Dark Web’s Role in Enabling Phishing Attacks

The dark web is a hidden part of the internet, only accessible through specialized software, and is often associated with illegal activities. For cybercriminals, it serves as a marketplace for trading stolen credentials, phishing kits, malware, and other hacking tools. It has become a hub where sensitive information, such as login credentials, personal data, and even company databases, are sold. This underground economy fuels the proliferation of phishing attacks by providing malicious actors easy access to the tools they need.
Phishing kits, which contain pre-packaged materials like fake login pages and email templates, are readily available for purchase on the dark web. These kits allow even inexperienced attackers to launch phishing campaigns with minimal effort. Additionally, malware and compromised credentials are frequently traded, enabling attackers to penetrate corporate systems with stolen data, particularly targeting small and medium-sized enterprises (SMEs) in the UAE. SMEs, with their limited resources, are often seen as easier targets by cybercriminals.
To mitigate this growing threat, dark web monitoring is becoming essential for businesses. By actively monitoring dark web forums and marketplaces, businesses can detect when their company’s data is being traded, allowing them to act before phishing attacks escalate. Regular security gap analysis combined with dark web monitoring helps businesses stay informed about vulnerabilities and implement preventative measures to prevent data breaches in small businesses.
| Common Dark Web Items | Impact on Businesses |
|---|---|
| Phishing Kits | Enables widespread phishing campaigns targeting employees |
| Stolen Credentials | Allows attackers to bypass security systems and compromise accounts |
| Malware | Can lead to ransomware attacks or data theft |
| Company Data | Data breaches, financial loss, and reputational damage |
Phishing Tactics Exploiting Security Gaps in UAE Businesses
Phishing attacks often succeed by exploiting security gaps within businesses, particularly those that lack comprehensive cybersecurity measures. These gaps may include outdated software, weak password policies, or untrained staff who are unaware of how to detect phishing attempts. For small and medium-sized enterprises (SMEs) in the UAE, the lack of proper cybersecurity services and infrastructure makes them especially vulnerable to phishing schemes.
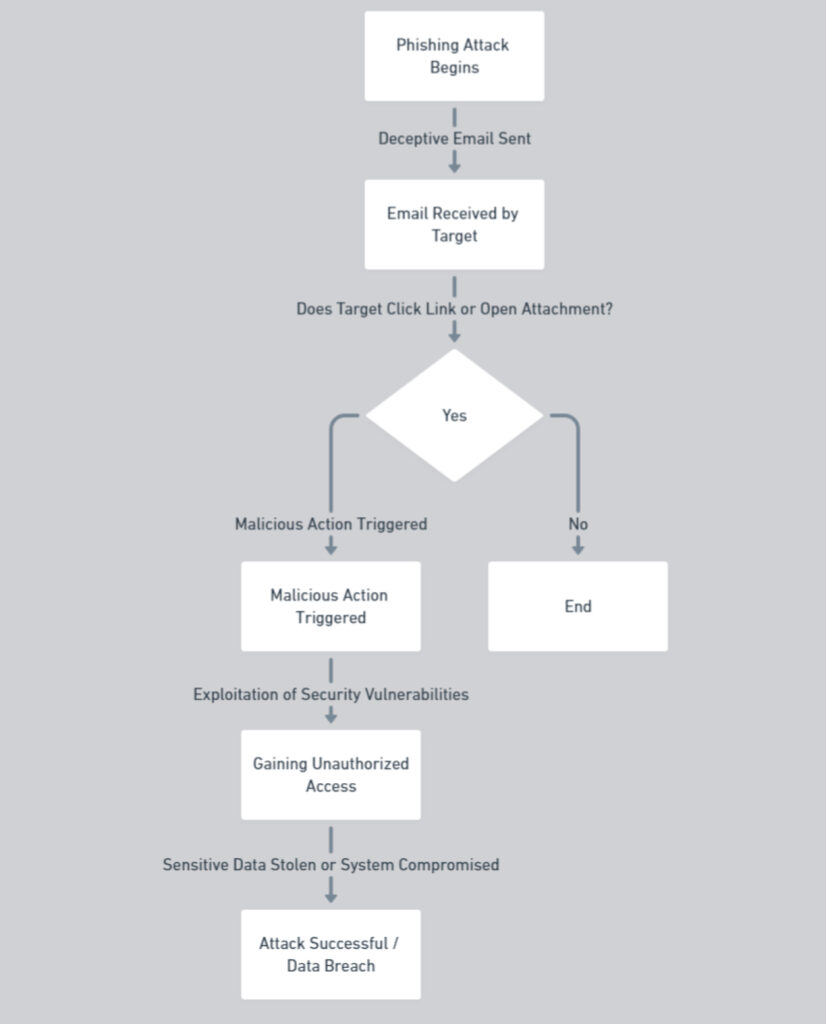
One of the most common attack vectors is phishing via email. Attackers typically send fraudulent emails disguised as legitimate communications, tricking recipients into revealing sensitive information such as login credentials or financial details. Employees are often the weakest link in this chain. Cybercriminals craft personalized emails that look authentic, using techniques like spoofing or impersonation to deceive staff members. Once an employee clicks on a malicious link or downloads a suspicious attachment, the attacker gains access to the company’s network, potentially leading to severe financial loss or data breaches. In one notable case, a UAE-based SME fell victim to an email phishing attack that resulted in over $500,000 in financial damage, demonstrating the real-world consequences of such vulnerabilities.
The importance of conducting regular security gap assessments cannot be overstated. A cybersecurity assessment allows businesses to identify weaknesses in their digital defenses and close gaps that phishing attackers could exploit. With the growing complexity of phishing tactics, UAE businesses need to be vigilant and ensure that their cybersecurity protocols are up-to-date. This involves not only technical solutions like firewalls and email filtering systems but also educating employees on how to recognize phishing emails.
Real-world examples show that businesses failing to address these security gaps are at high risk. In a recent incident, a UAE healthcare provider was targeted by a spear-phishing attack that compromised the personal data of hundreds of patients. The attack was traced back to a lack of multi-factor authentication and regular security audits, highlighting the need for comprehensive cybersecurity services for small businesses to prevent similar breaches.
A security gap assessment provides businesses with a clear roadmap to strengthening their defenses and mitigating the risks posed by phishing. Without it, businesses leave themselves exposed to one of the top cybersecurity threats facing organizations today.
Proactive Phishing Prevention Strategies

In the face of rising phishing threats, UAE businesses must adopt proactive strategies to prevent attacks before they cause significant harm. Dark web monitoring is one such approach. By actively scanning the dark web for compromised credentials or company-related information, businesses can detect phishing risks early and take immediate action. Monitoring the dark web enables businesses to see when their data or credentials are being traded, allowing them to prevent attacks before they even begin. For small and medium-sized enterprises (SMEs) without internal resources, outsourcing dark web monitoring to a managed cybersecurity provider is a viable and effective option.
Employee training and awareness are also crucial in combating phishing. Phishing attacks often target employees, tricking them into clicking malicious links or revealing sensitive information. To mitigate this risk, businesses must prioritize continuous employee education. Regular workshops or simulated phishing attacks help employees recognize common phishing tactics and strengthen their role as the first line of defense. Awareness training can significantly reduce the likelihood of successful phishing attempts by empowering employees to spot fraudulent emails and suspicious links.
Implementing advanced cybersecurity measures is equally important. Endpoint protection solutions safeguard devices from malicious software, while multi-factor authentication (MFA) adds an extra layer of security by requiring additional verification steps beyond a password. Email filtering systems can automatically detect and block phishing attempts before they reach employees’ inboxes. Combining these tools creates a robust cybersecurity infrastructure that minimizes vulnerabilities. Regular cybersecurity risk assessments are essential for evaluating the effectiveness of these measures and ensuring that security protocols remain up-to-date. Businesses should also develop incident response plans to quickly respond to any breaches that may occur.
For businesses lacking in-house expertise, the role of cybersecurity services cannot be overstated. Outsourcing to managed security providers allows companies to regularly conduct security gap assessments, monitor the dark web, and implement best practices for defending against phishing. These providers can offer the best cyber security for small businesses, tailored to meet specific organizational needs. By engaging external experts, businesses can ensure a comprehensive cybersecurity strategy is in place, even without the resources for a full-time IT security team.
| Phishing Prevention Strategies | Benefits |
|---|---|
| Employee Training | Reduces the risk of employees falling for phishing attacks |
| Dark Web Monitoring | Detects stolen credentials early and mitigates threats |
| Multi-Factor Authentication (MFA) | Adds extra security to accounts, reducing the chances of breaches |
| Email Filtering | Automatically blocks suspicious emails before they reach employees |
| Regular Cybersecurity Assessments | Identifies vulnerabilities and strengthens security measures |
In conclusion, a multi-layered approach combining dark web monitoring, employee training, and advanced cybersecurity tools is the most effective way for UAE businesses to protect against phishing. For companies without the necessary internal resources, outsourcing to cybersecurity services for small businesses ensures they stay ahead of evolving threats. Proactive prevention is the key to avoiding financial and reputational damage caused by phishing attacks.
Compliance with UAE Cybersecurity Regulations

The UAE’s regulatory framework for cybersecurity is anchored by two primary authorities: the National Electronic Security Authority (NESA) and the Telecommunications Regulatory Authority (TRA). These bodies have established strict guidelines to ensure that businesses operating in the UAE, particularly those in critical sectors, implement robust cybersecurity measures. NESA’s UAE Information Assurance Standards (IAS) outline requirements for protecting critical national infrastructure, while TRA’s regulations ensure that telecom operators and related businesses comply with cybersecurity standards to safeguard data and communications.
For businesses, especially small and medium-sized enterprises (SMEs), complying with these regulations is essential not only to avoid potential penalties but also to protect customer data. Failure to meet cybersecurity standards can result in significant financial and reputational damage. Furthermore, non-compliance can lead to disruptions in business operations, fines, and the loss of trust from customers and partners.
Dark web intelligence and regular cybersecurity assessments play a critical role in helping businesses maintain compliance. Monitoring the dark web allows businesses to detect potential breaches early, while routine security gap assessments help identify vulnerabilities that could lead to non-compliance. SMEs can also take advantage of free cybersecurity resources and outsourced cybersecurity services to ensure they remain compliant without overextending their internal resources. By proactively addressing risks, SMEs can comply with UAE cybersecurity regulations and avoid the severe consequences of a breach.
Future-Proofing UAE Businesses Against Phishing
As phishing threats continue to evolve in sophistication, UAE businesses must take a proactive approach to cybersecurity. The increasing reliance on digital platforms makes it essential to adopt advanced cybersecurity strategies that include dark web monitoring, employee training, and regular cybersecurity assessments. By closing security gaps and staying vigilant, businesses can reduce their exposure to phishing attacks that could cause significant financial and reputational harm.
To stay ahead of these threats, companies should actively engage in phishing prevention strategies, such as multi-factor authentication and email filtering, while ensuring they conduct thorough cybersecurity risk assessments. This approach helps prevent data breaches in small businesses and strengthens overall resilience against cyberattacks.
For businesses that lack in-house expertise, seeking professional cybersecurity services is a crucial step. Partnering with experts ensures that organizations are equipped with the best cybersecurity solutions tailored to their unique needs. Proactively investing in cybersecurity not only protects assets but also ensures compliance with UAE’s regulations.
To safeguard your business and future-proof against phishing attacks, it’s time to consult with cybersecurity professionals who can offer comprehensive advice and protection.
Categorized in:
Comments