
Understanding the Dark Web and Its Relevance to UAE Businesses
The Dark Web represents a hidden portion of the internet that is deliberately concealed and accessible only through specialized software, like the Tor browser. While the Surface Web accounts for a mere 4% of internet content, the Deep Web encompasses nearly 90%, leaving the remaining 6% to the Dark Web. This obscure space is often associated with illicit activity, serving as a marketplace for stolen data, hacking services, and counterfeit documents, which pose significant risks for businesses globally, including those in the UAE.
For UAE business owners, the Dark Web is more than an abstract threat. It functions as a dynamic criminal ecosystem where sensitive corporate information, such as customer data and intellectual property, can be traded among cybercriminals. In 2023, for instance, reports showed that over 60% of small businesses faced data breaches, many of which were traced back to data exposed on the Dark Web. As data breaches continue to rise, understanding the structure and risks of the Dark Web has become essential for businesses seeking effective cybersecurity measures.
A deeper understanding of this part of the internet provides insight into how cybersecurity practices, such as continuous monitoring and proactive data protection, can safeguard businesses against risks originating from the Dark Web.
Types of Criminal Activities on the Dark Web Impacting Businesses

The Dark Web has become a haven for various types of criminal activities targeting businesses, especially those in the UAE. Understanding these threats is crucial for small businesses as they are frequently targeted due to perceived vulnerabilities and limited cybersecurity resources. Here, we detail some of the most pressing cyber threats that UAE businesses face on the Dark Web.
1. Data Breaches and Stolen Credentials
Data breaches on the Dark Web are rampant, often involving the sale of sensitive information such as customer data, financial records, and corporate emails. Small businesses are frequently the victims of these breaches, with a 2022 study revealing that 43% of data breaches impacted small businesses globally. Exposed credentials can be purchased cheaply on the Dark Web, allowing cybercriminals to infiltrate business systems and compromise operations. For a more in-depth look, refer to the Cybersecurity Journal’s report on data breaches and their Dark Web origins.
2. Identity Theft and Corporate Espionage
Identity theft extends beyond individuals, affecting businesses through compromised corporate identities and employee information. Criminals often use this data to create fake business accounts, make unauthorized transactions, or engage in corporate espionage. For example, sensitive documents like business plans or proprietary data are sometimes available for purchase. This growing trend has led many UAE businesses to increase their focus on cybersecurity risk assessment and regular Dark Web monitoring.
3. Illegal Trade and Intellectual Property Theft
The illegal trade of stolen intellectual property (IP) is another major threat, as it involves sensitive designs, patents, and trade secrets being sold or auctioned on the Dark Web. Businesses in industries such as technology and manufacturing are particularly vulnerable, as their IP holds high value. A thorough security gap analysis can help companies identify and secure these high-risk assets to prevent exploitation.
Here is a detailed table summarizing common criminal activities on the Dark Web, along with examples and potential impacts on businesses:
| Type of Criminal Activity | Example | Potential Impact on Businesses |
|---|---|---|
| Data Breaches | Sale of customer data, financial records, and employee credentials | Loss of customer trust, potential regulatory fines, costly remediation efforts |
| Identity Theft | Use of employee or corporate identities to create fake accounts | Unauthorized transactions, reputational damage, potential legal liabilities |
| Corporate Espionage | Sale of sensitive business plans or proprietary designs | Loss of competitive advantage, financial losses, potential intellectual property theft |
| Illegal Trade of Intellectual Property | Auctioning of patents, designs, or other IP assets | Loss of intellectual property, reduced market share, weakened brand value |
| Ransomware-as-a-Service (RaaS) | Offering ransomware tools for targeted attacks on businesses | Data encryption and ransom demands, business disruption, significant financial loss |
| Phishing Kits and Malware | Sale of phishing tools, malware, and exploit kits targeting businesses | Increased vulnerability to cyber attacks, data theft, and system compromise |
To safeguard against these threats, many cybersecurity experts recommend a gap analysis cyber security approach and regular cybersecurity assessment protocols, which help businesses uncover vulnerabilities before they’re exploited.
How UAE Businesses Are Targeted and Impacted
UAE businesses face distinct cyber threats due to their rapid digital adoption and the region’s high-value economy, making them a primary target on the Dark Web. Cybercriminals often exploit security gaps to gain unauthorized access to valuable data and systems, with consequences that include severe financial and reputational losses. Small and medium-sized businesses (SMBs) are particularly vulnerable, often lacking the resources for comprehensive cybersecurity measures. Conducting a security gap analysis can help identify these vulnerabilities and protect these businesses from potential exploitation.
One prominent threat is the unauthorized sale of corporate data on the Dark Web, where compromised data often ends up after a breach. In a recent report by the UAE’s Telecommunications and Digital Government Regulatory Authority, it was noted that cyberattacks against businesses in the UAE have risen sharply, costing SMBs millions of dirhams in breach recovery. Beyond monetary losses, these breaches also result in reputational damage, eroding customer trust and impacting long-term business viability. The best cyber security for small business solutions emphasize proactive steps, such as continuous monitoring and regular security assessments, to prevent such threats.
The interconnectedness of business systems also poses additional risks, as cybercriminals leverage Dark Web data to launch phishing attacks, ransomware, and other malicious activities. A structured security gap assessment allows UAE businesses to identify areas for improvement, safeguarding both their operational integrity and customer trust.
Signs Your Business Data May Be on the Dark Web

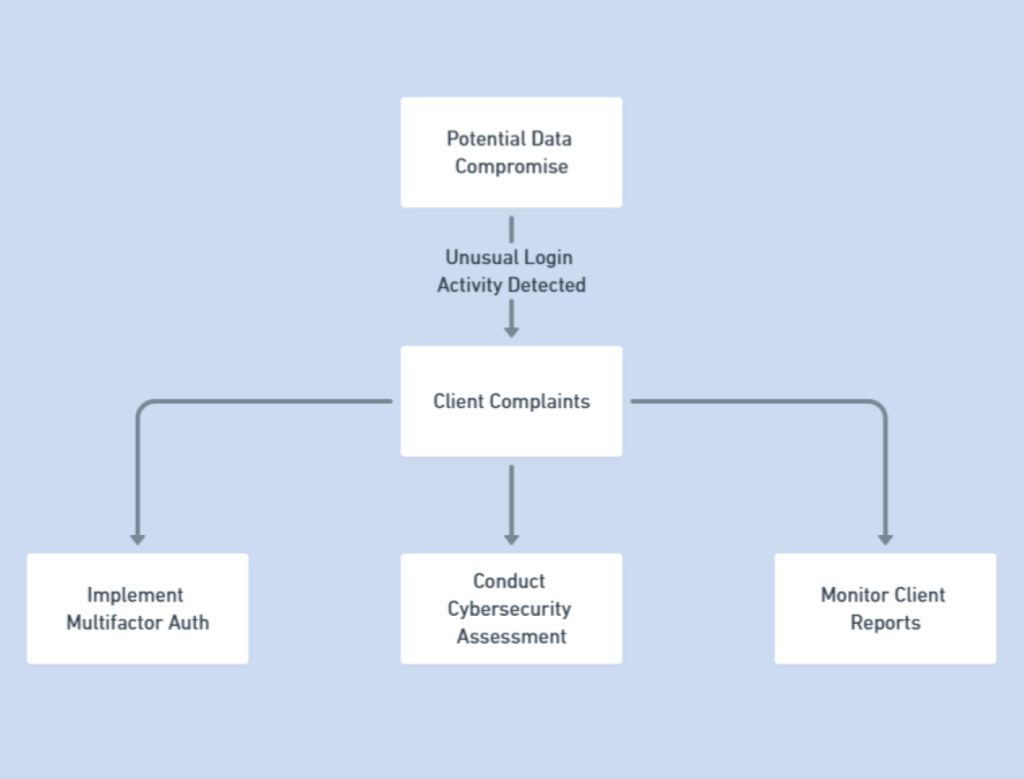
For UAE business owners, early detection of compromised data is crucial to mitigate damage and protect sensitive information. Certain indicators suggest that a business’s data may have found its way onto the Dark Web. One primary warning sign is unusual login activity, especially from unfamiliar IP addresses or unexpected locations, as it may indicate stolen credentials being used by unauthorized parties. Business owners should monitor login logs closely and establish alerts for any suspicious access patterns.
Another red flag is if clients report unusual activity associated with their accounts, such as unauthorized transactions or communication they did not initiate. Such reports can often point to data leakage, where criminals on the Dark Web may have obtained and exploited client information. Regularly reviewing customer feedback and promptly addressing complaints can help prevent data breaches small businesses might otherwise overlook.
Finally, notable decreases in system performance or unexpected changes in data storage could signal the presence of malware, possibly introduced to collect or transmit business data to illicit networks. A thorough cybersecurity risk assessment can help pinpoint potential vulnerabilities before they are exploited.
Protecting Your Business from Dark Web Threats
To safeguard UAE businesses from the threats posed by the Dark Web, implementing robust cybersecurity practices is essential. Here are practical steps that businesses can take to minimize the risk of their data being leaked or sold:
- Regular Cybersecurity Assessments
Conducting frequent cybersecurity assessments helps identify vulnerabilities within the company’s infrastructure. By understanding weak points, businesses can take proactive steps to secure sensitive data. This measure is critical for small businesses that may lack the resources for advanced cybersecurity systems. Free cybersecurity resources for small businesses, such as online tools and templates from government cybersecurity agencies, are valuable starting points. - Employee Training and Awareness Programs
Employees are often the first line of defense against cyber threats. Training them to recognize phishing attempts, suspicious links, and other social engineering tactics can reduce the likelihood of data leaks. A comprehensive employee training program should be a priority when choosing the best cybersecurity solution for small business needs. - Implementing Multifactor Authentication (MFA)
Multifactor Authentication adds an extra layer of security, making it harder for unauthorized users to access company systems. For instance, requiring both a password and a code sent to a trusted device can prevent cybercriminals from using stolen credentials to breach accounts. - Dark Web Monitoring Services
Dark Web monitoring services alert businesses if their data appears on illicit marketplaces or forums. Services like these enable companies to react promptly to potential breaches and secure exposed data. For small businesses looking to prevent data breaches, many cybersecurity providers offer affordable monitoring tools tailored to limited budgets. - Data Encryption and Regular Backups
Encrypting sensitive data ensures that even if it is accessed illegally, it remains unreadable without the decryption key. Regular data backups are also essential for quick recovery in case of a ransomware attack or data breach.
| Preventive Measure | Description | Effectiveness |
|---|---|---|
| Regular Cybersecurity Assessments | Identifies vulnerabilities in the business’s infrastructure to proactively address potential risks. | High - Reduces exposure to security weaknesses. |
| Employee Training and Awareness | Educates employees on recognizing phishing and social engineering tactics to prevent data leaks. | High - Reduces human error as a source of cyber threats. |
| Multifactor Authentication (MFA) | Adds an extra layer of security to accounts, making it difficult for unauthorized access. | High - Strongly enhances login security. |
| Dark Web Monitoring Services | Alerts the business if its data appears on the Dark Web, allowing for prompt response actions. | Moderate - Early warning system for potential data leaks. |
| Data Encryption and Regular Backups | Ensures data is secure even if accessed illegally; backups aid recovery from cyber incidents. | High - Protects data integrity and supports quick recovery. |
For businesses looking to secure their operations on a budget, a gap analysis cyber security approach can help in prioritizing resources effectively. For more in-depth guidance, consult free cybersecurity resources for small businesses available through agencies like the UAE’s Cybersecurity Council and global organizations.
Choosing the Right Cybersecurity Solution for Small Businesses

For small businesses, selecting the right cybersecurity solution involves understanding specific vulnerabilities and balancing affordability with effectiveness. Small companies often lack the resources of larger organizations, so finding the best cyber security for small business means prioritizing tools that are straightforward, cost-effective, and comprehensive. Conducting a gap analysis cyber security assessment can help identify the most pressing vulnerabilities, guiding business owners toward solutions that address their unique security needs.
Cybernod offers tailored cybersecurity services that cater to small businesses, providing a blend of essential features such as firewall protection, antivirus management, and employee training resources. Their scalable solutions grow with the business, making Cybernod an adaptable choice for companies expecting expansion. Additionally, Cybernod provides Dark Web monitoring to alert businesses if sensitive data surfaces on illicit networks, a critical feature to prevent data breaches small businesses might face.
By choosing a cybersecurity solution that aligns with their needs and resources, small businesses can secure their operations against cyber threats, ensuring continuity and protecting client trust.
Leveraging Dark Web Monitoring Services

Dark Web monitoring services have become essential for businesses seeking proactive protection against data breaches. These services continuously scan the Dark Web for exposed or stolen data, allowing companies to respond quickly if any sensitive information appears in underground marketplaces. By integrating Dark Web monitoring with a cybersecurity assessment, businesses can enhance their ability to detect vulnerabilities and improve their security posture.
For small businesses, Dark Web monitoring provides an early warning system against potential breaches. If an organization’s data, such as login credentials or customer information, is detected, immediate alerts enable rapid action to mitigate risks. This layer of monitoring is especially valuable for small companies that may lack the resources for an extensive security infrastructure. By detecting exposed data early, these businesses can take swift steps to secure their systems, reset compromised credentials, and notify affected customers as necessary.
Dark Web monitoring services work seamlessly within existing security gap assessment processes, identifying areas where further protections may be needed. For example, Cybernode offers Dark Web monitoring as part of its cybersecurity solutions, scanning hidden parts of the internet and notifying clients of any detected threats. This Cybernode Dark Web Monitoring Service ensures that small businesses are protected and informed of risks in real-time.
By leveraging these monitoring services, small businesses can take proactive measures to defend their operations, minimizing the impact of potential breaches and reinforcing customer trust.
For a deeper exploration of dark web monitoring and its benefits for UAE businesses, especially regarding cost-effective solutions for small businesses, we recommend reading our detailed article: [ Protecting Your Business Identity: The Importance of Dark Web Monitoring in the UAE ]
Taking Action to Protect UAE Businesses from Dark Web Threats
Proactive cybersecurity measures and Dark Web monitoring are vital for UAE businesses to protect their data and maintain customer trust. With the growing threat landscape, businesses must ensure they comply with cybersecurity regulations, safeguard sensitive information, and prevent unauthorized access. By investing in cybersecurity assessments and monitoring solutions, companies can detect vulnerabilities early and address potential risks before they escalate. For UAE businesses, taking these actions is not only a protective measure but also a step towards sustainable growth. To enhance your security posture, consider consulting with experts to implement tailored cybersecurity solutions today.
Categorized in:
Comments