
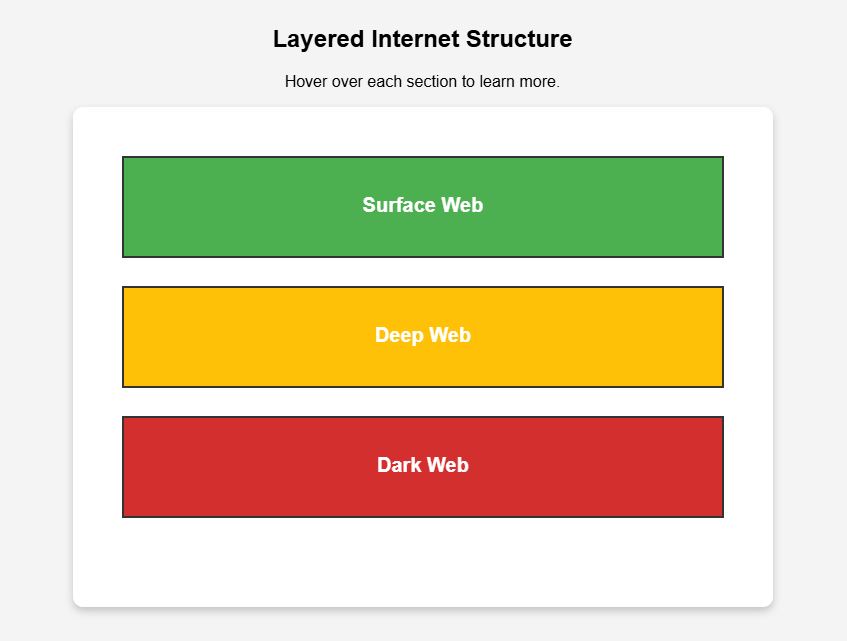
The dark web is a concealed segment of the internet that requires specialized software, such as Tor (The Onion Router), to access. Unlike the surface web, which search engines index and make easily accessible, or the deep web, which includes private databases and corporate intranets, the dark web operates anonymously and is often associated with illicit activities.
However, not all content on the dark web is unlawful. Whistleblower platforms like SecureDrop and privacy-focused communities use it to safeguard free speech. Despite this, cybercriminal activity thrives, with over 24 billion exposed credentials circulating in underground forums (Digital Shadows, 2022).
Businesses cannot afford to ignore the dark web. Compromised employee login details, leaked customer data, and stolen intellectual property frequently surface in darknet marketplaces. A proactive cybersecurity assessment can help small businesses identify security gaps and mitigate potential breaches before they escalate.
How the Dark Web Works: Understanding Its Infrastructure

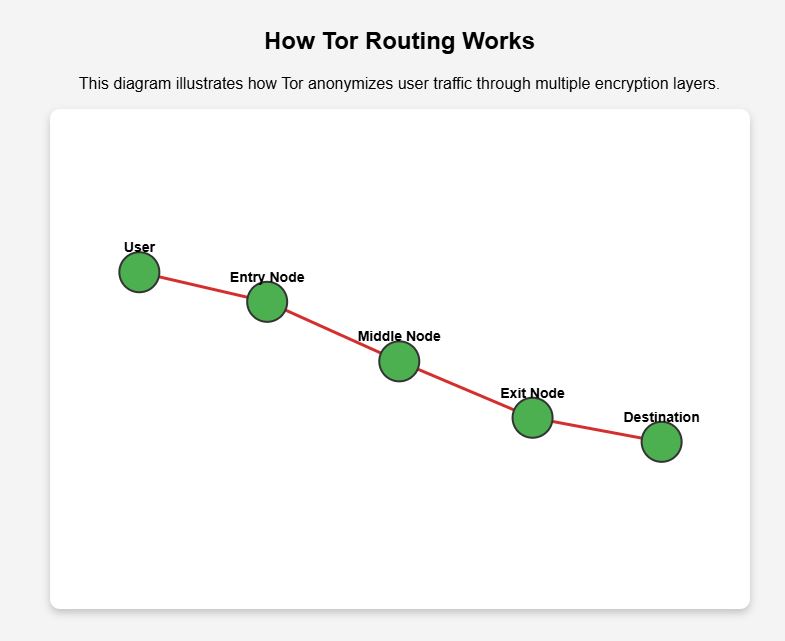
The dark web operates on anonymizing networks, the most well-known being Tor (The Onion Router). Unlike traditional internet routing, which directly connects users to websites, Tor encrypts and reroutes traffic through multiple volunteer-operated nodes, concealing users’ identities and locations. This layered encryption makes cybersecurity risk assessment challenging for law enforcement and security analysts.
Comparing Tor, I2P, and Freenet
- Tor: Primarily used for anonymous web browsing. It routes traffic through a decentralized network, encrypting data multiple times before reaching its destination.
- I2P (Invisible Internet Project): Optimized for anonymous peer-to-peer (P2P) communication. It is widely used for secure file sharing and messaging.
- Freenet: A distributed censorship-resistant platform where data is stored in a decentralized manner, making content retrieval independent of real-time connections.
Why Special Software is Required
Unlike the surface web, which standard browsers like Chrome or Firefox access, dark web sites use .onion domains, which require a Tor-enabled browser to navigate securely. This ensures user anonymity, but also facilitates illicit activities, increasing the importance of security gap analysis in monitoring threats.
What You Can Find on the Dark Web
The dark web is often associated with criminal activity, but it also serves as a platform for legitimate uses. Understanding both its legal and illegal content is essential for businesses conducting cybersecurity risk assessments.
Legal Content on the Dark Web
Some platforms leverage the dark web to protect privacy and free speech:
- Whistleblowing platforms like SecureDrop allow journalists and activists to securely communicate without exposing their identities.
- Privacy-focused forums discuss encryption, surveillance risks, and data protection.
- Political activism resources offer individuals in censorship-heavy regions a means to express their views without government interference.
- Research archives contain academic papers and restricted government publications.
Illegal Content on the Dark Web
The dark web also facilitates criminal activities, including:
- Stolen data markets where compromised credentials, corporate information, and financial records are sold.
- Illicit marketplaces trading drugs, counterfeit goods, firearms, and hacking tools.
- Hacker forums where cybercriminals sell malware, exploit kits, and ransomware-as-a-service.
While the dark web can be a source of threats, vulnerabilities exist in other emerging technologies as well. Blockchain, while promising, is not immune to security risks. Smart contracts, the foundation of many blockchain applications, can contain vulnerabilities that lead to significant losses. To learn more about how penetration testing can fortify blockchain security and mitigate these risks, see our in-depth article: “The Hidden Risks of Blockchain: How Penetration Testing Fortifies Smart Contracts“.
The table below contrasts the lawful and unlawful aspects of dark web activities.
Legal vs. Illegal Uses of the Dark Web
| Legal Uses | Illegal Uses |
|---|---|
| Whistleblowing platforms (e.g., SecureDrop) | Stolen data markets (selling leaked credentials and financial records) |
| Privacy-focused forums and encrypted communication | Illicit marketplaces for drugs, counterfeit goods, and hacking tools |
| Political activism and information-sharing in censored regions | Hacker forums offering cybercrime services, including malware and ransomware |
| Research archives and academic papers | Illegal financial transactions, money laundering, and fraud |
How Businesses Are Affected by the Dark Web

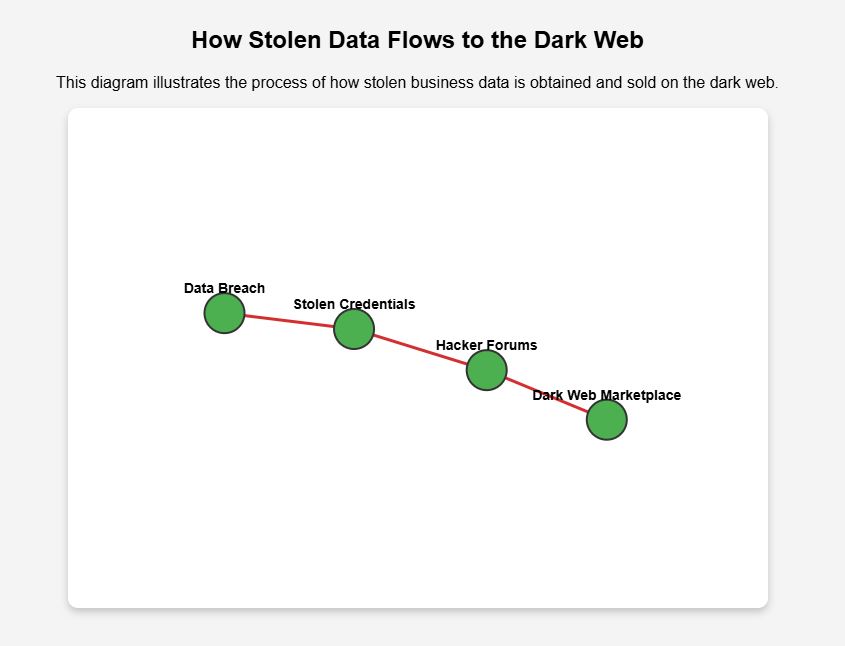
The dark web serves as a hub for stolen business data, with compromised credentials, intellectual property, and financial records frequently being sold. Small and medium-sized enterprises (SMEs) are particularly vulnerable, as they often lack comprehensive cybersecurity measures.
Exposed Credentials and Data Breaches
Cybercriminals acquire login credentials through phishing attacks, malware infections, or breaches and sell them on dark web marketplaces. Tools like Have I Been Pwned help businesses check if their email addresses or passwords have been leaked. Once credentials are exposed, attackers can exploit them for unauthorized access, financial fraud, or identity theft.
Corporate Espionage and Dark Web Threats
Competitors or cybercriminals may purchase sensitive corporate data, including trade secrets, research files, and internal communications. This type of cyber espionage can significantly impact a company’s market competitiveness and reputation.
Why Small Businesses Are at Risk
Small businesses often lack dedicated cybersecurity teams and rely on outdated security protocols. Without regular security gap assessments, they become easy targets for cybercriminals looking for low-hanging fruit.
How to Protect Yourself and Your Business from Dark Web Threats

Cybercriminals frequently exploit stolen credentials and company data on the dark web, leading to financial losses, regulatory penalties, and reputational damage. Businesses must implement proactive strategies to prevent data breaches and comply with cybersecurity regulations.
Dark Web Monitoring: Identifying Stolen Credentials
Monitoring for leaked employee credentials, customer information, and intellectual property on the dark web is essential. Services like dark web scanning tools and databases such as NIST Cybersecurity Framework offer best practices to help businesses detect unauthorized data exposure.
Dark Web Monitoring: Identifying Stolen Credentials
Weak or reused passwords are a primary cause of credential theft. Implementing MFA, enforcing strong password policies, and using password managers significantly reduce the risk of compromised accounts.
Security Awareness Training for Employees
Phishing attacks remain a major vector for data breaches in small businesses. Regular security awareness training helps employees recognize social engineering tactics, malicious emails, and suspicious links, preventing unauthorized access.

The Future of the Dark Web & Cybersecurity Awareness
Governments and law enforcement agencies are intensifying efforts to monitor and disrupt cybercriminal activities on the dark web. Interpol, Europol, and national cybersecurity divisions leverage machine learning, blockchain analytics, and AI-driven threat intelligence to detect illegal transactions and malicious actors. However, businesses cannot solely rely on law enforcement for protection.
Proactive cybersecurity for small businesses is crucial, as stolen credentials, financial records, and intellectual property are frequently traded on the dark web. Organizations must implement continuous cybersecurity assessments to detect security vulnerabilities before exploitation occurs.
Investing in dark web monitoring, security awareness training, and multi-factor authentication is essential for protecting sensitive business assets. At Cybernod, we offer comprehensive cybersecurity assessments and real-time threat intelligence to help businesses stay ahead of cyber risks. Secure your organization today—contact Cybernod for a tailored cybersecurity solution.
Categorized in: