
The deep web, a vast and largely uncharted section of the internet, accounts for an estimated 90% of all online content. Unlike the surface web, which is accessible through standard search engines, the deep web consists of data hidden behind paywalls, private databases, and password-protected systems. This includes critical resources like academic research archives, financial records, and government databases—information that is not indexed or readily available to the average user.
Despite its legitimate purposes, the deep web holds significant implications for businesses, particularly in the realm of cybersecurity. For example, sensitive corporate information, such as intellectual property or employee credentials, may inadvertently become accessible on the deep web due to poor security measures. A 2023 report revealed that over 30% of small businesses experienced data breaches stemming from improperly secured databases, highlighting the importance of regular cybersecurity assessments.
It is crucial to distinguish the deep web from the dark web, often associated with illicit activities. While the deep web encompasses secure, legitimate content, the dark web represents a smaller, more concealed subset where anonymity is leveraged for illegal transactions and cybercrime.
A clear understanding of the deep web, paired with robust cybersecurity strategies, enables businesses to protect their digital assets and identify potential vulnerabilities. Including a structured approach to cybersecurity services, such as regular assessments and risk evaluations, is essential for safeguarding sensitive information.
What is the Deep Web?
The deep web refers to the portion of the internet that is not indexed by standard search engines such as Google or Bing. Unlike the surface web, which hosts publicly accessible content, the deep web includes data hidden behind authentication or paywalls. Examples of deep web content range from subscription-based services like streaming platforms and online journals to private databases, financial records, and academic papers stored in university archives.
A significant misconception about the deep web is its association with illegal activities. While this is true for the dark web, a smaller subset of the deep web, the majority of the deep web consists of legitimate and highly valuable information. Businesses often rely on the deep web for accessing proprietary tools, conducting research, and safeguarding sensitive records. For instance, academic institutions use the deep web to store research publications and studies, which are crucial for scholarly and scientific advancements. According to Comparitech, using deep web search engines like Base or CORE can provide access to a wealth of academic resources, fostering innovation while avoiding surface web limitations.
From a cybersecurity perspective, the deep web holds potential risks if not managed appropriately. Unsecured databases or poorly protected platforms can expose sensitive data, making businesses vulnerable to breaches. Conducting a gap analysis cyber security assessment ensures that such vulnerabilities are identified and mitigated effectively. Moreover, businesses can leverage free cybersecurity resources for small businesses to strengthen their digital defenses.
| Category | Description | Examples |
|---|---|---|
| Private Databases | Data stored in secure, non-public platforms. | Medical records, financial systems |
| Subscription Services | Content accessible through paid memberships. | Streaming platforms, research journals |
| Academic Resources | Repositories of scholarly papers and studies. | University archives, CORE |
| Internal Business Tools | Confidential platforms used within organizations. | Employee portals, CRM systems |
How the Deep Web Impacts Cybersecurity

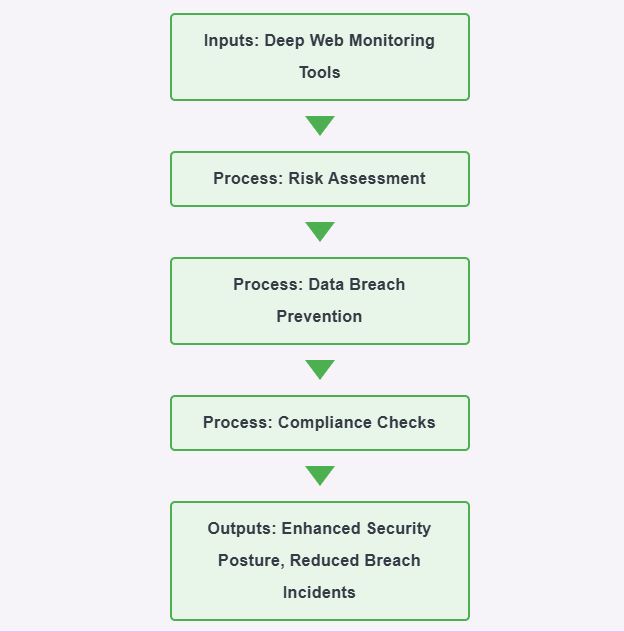
Monitoring the deep web is a crucial component of a robust cybersecurity risk assessment strategy. The deep web serves as a repository for both legitimate and potentially compromised data, making it a critical area for identifying vulnerabilities. For small businesses, where resources for cybersecurity are often limited, neglecting this layer can expose sensitive information to malicious actors. Data breaches, which affect nearly 43% of small businesses annually, frequently originate from unsecured databases or leaked credentials on the deep web.
Deep web monitoring provides actionable insights that can prevent data breaches for small businesses. For instance, by identifying stolen login credentials, businesses can act preemptively to secure accounts. Such insights are vital for complying with regulatory standards, such as Australia’s Privacy Act or the UAE’s cybersecurity mandates, ensuring businesses comply with cybersecurity regulations. Proactive monitoring reduces the likelihood of regulatory penalties and reputational damage.
Effective cybersecurity strategies leverage advanced tools and methods to harness the deep web’s insights. Specialized software, such as dark web scanners and data leak detection tools, identifies exposed credentials, sensitive files, and insider threats. Additionally, integrating deep web monitoring with broader cybersecurity frameworks, such as penetration testing and cybersecurity risk assessments, ensures comprehensive protection.
To fully illustrate the role of deep web monitoring in a cybersecurity strategy, businesses can visualize its integration using a flowchart. For example, the chart can depict how monitoring feeds into risk assessments, threat mitigation, and regulatory compliance efforts.
Read Now:
While monitoring the deep web is crucial, it’s equally important to understand and address the specific threats emanating from the dark web. To learn more about how dark web scanners can protect your business from these threats, read our in-depth article: “Protect Your Data: Understanding Dark Web Scanners and Their Role in Cybersecurity.“
Key Features and Tools for Accessing the Deep Web

Accessing the deep web requires specialized tools and search engines designed to retrieve content not indexed by conventional search platforms like Google. Unlike the surface web, where content is freely available, the deep web includes a wealth of legal and beneficial information such as government records, academic papers, and subscription-based resources.
Search engines tailored for deep web exploration provide enhanced privacy and access to otherwise inaccessible data. For instance, DuckDuckGo ensures user anonymity while delivering results from various deep web sources, making it a valuable tool for research and privacy-conscious users. Similarly, StartPage combines advanced search functionalities with robust privacy protections, enabling businesses to conduct secure and targeted searches.
These tools are indispensable for accessing content that supports tasks like security gap analysis and security gap assessment. Small businesses can utilize these resources to evaluate their cybersecurity posture while exploring deep web platforms for industry-specific insights. Additionally, academic databases and government archives accessed through the deep web can aid in identifying compliance standards, helping businesses choose the best cybersecurity solution tailored to their needs.
| Search Engine | Key Features | Website Link |
|---|---|---|
| DuckDuckGo | Focus on user privacy, no search tracking, access to deep web content. | Visit DuckDuckGo |
| StartPage | Advanced search functionality, private browsing, results from non-indexed sources. | Visit StartPage |
| CORE | Access to academic papers and research repositories. | Visit CORE |
| Base | Extensive database for academic and scholarly articles. | Visit Base |
By leveraging these tools, businesses and researchers can navigate the deep web safely and effectively, ensuring compliance with security standards and accessing valuable resources for decision-making.
Risks and Challenges of Deep Web Navigation

While the deep web offers access to valuable and legitimate resources, navigating its vast and hidden content comes with inherent risks. Unverified websites and unsecured platforms often lurk within the deep web, posing threats such as data breaches, malware infections, and phishing attacks. For small businesses, these risks can escalate into severe consequences, including financial losses and reputational damage. The absence of proper safeguards increases exposure to cyberattacks, underlining the importance of deploying cybersecurity for small businesses tailored to address such vulnerabilities.
A common challenge arises when users inadvertently access illegal or harmful content. Even unintentional visits to these areas can result in legal liabilities or exposure to malicious actors. For instance, poorly secured databases on the deep web can lead to sensitive information being compromised. Such scenarios highlight the critical need for implementing the best cybersecurity for small businesses, encompassing secure browsing practices, endpoint protection, and threat monitoring.
Adopting robust cybersecurity measures is essential for safe exploration of the deep web. Using Virtual Private Networks (VPNs), endpoint protection software, and trusted search engines like DuckDuckGo can mitigate risks significantly. Additionally, resources like HackerNoon provide valuable insights into navigating the deep web securely, including step-by-step guides for accessing legitimate content safely.
By prioritizing security and employing proactive measures, businesses can leverage the deep web’s potential without compromising their digital assets. Combining advanced tools with education on secure navigation is the foundation of a resilient cybersecurity strategy.
The Deep Web’s Role in Business and Cybersecurity
The deep web presents a significant opportunity for businesses to access hidden resources and enhance their cybersecurity strategies. It is a repository of valuable content, including private databases, academic research, and secure platforms, that can empower small businesses to address top cybersecurity threats small businesses encounter. By leveraging the deep web for legitimate purposes, organizations can gain insights to strengthen their defenses against cyberattacks and comply with regulatory requirements.
However, navigating the deep web requires caution. Unsecured access can expose businesses to risks such as data breaches and malware attacks. To comply with cybersecurity regulations small businesses must adhere to, organizations need robust measures in place. Professional cybersecurity assessments are essential for identifying vulnerabilities, safeguarding critical information, and ensuring adherence to legal and industry standards.
At Cybernod, we specialize in providing comprehensive cybersecurity solutions tailored to your business needs. Our professional assessments include deep web monitoring to detect potential risks and offer actionable insights to secure your digital assets. Visit Cybernod to learn how our services can help your business unlock the potential of the deep web while mitigating its risks.
Categorized in:
Comments