
Safeguarding Your Finances in the Digital Age
The United Arab Emirates (UAE) is embracing the digital era, offering a vibrant landscape for businesses of all sizes to thrive. However, this interconnectedness also presents a burgeoning threat: cybercrime. Malicious actors are constantly devising sophisticated methods to exploit vulnerabilities in IT systems, potentially leading to devastating financial losses for businesses.
According to the surge in cybercrimes targeting UAE businesses, cybersecurity risk assessments are paramount for safeguarding data and IT infrastructure. These comprehensive evaluations act as a protective shield, identifying weaknesses in your systems and data security practices. By proactively addressing these vulnerabilities, businesses can significantly reduce their attack surface and prevent cyberattacks from translating into financial ruin.
For insights into the escalating cybercrime landscape in the UAE, refer to the UAE government cybercrime resources. These resources provide valuable information on cyber safety and security practices tailored to businesses operating in the UAE. Additionally, the State of the UAE Cybersecurity Report 2024 offers a detailed analysis of the cybersecurity landscape, including statistics on cyberattacks and recommendations for businesses.
In this article, we’ll delve into the critical role of cybersecurity risk assessments for businesses in the UAE. We’ll explore the key steps involved in conducting a risk assessment, provide practical best practices specifically for UAE businesses, and highlight the financial benefits of proactive risk management. By implementing these strategies, businesses can navigate the digital landscape with confidence, safeguarding their valuable assets and ensuring a secure future in the ever-evolving digital realm.
The Cost of Cybercrime for UAE Businesses

The financial impact of cybercrime on UAE businesses can be crippling. Beyond the immediate costs of resolving the attack itself, businesses face a multitude of financial losses. Data breaches, a prevalent cyber threat, can expose sensitive customer information, leading to hefty fines for non-compliance with data privacy regulations like the UAE’s Data Protection Law. Additionally, reputational damage from a data breach can erode customer trust and loyalty, resulting in lost sales and hindered future growth.
Ransomware attacks, another costly cyber threat, encrypt critical business data, halting operations until a ransom is paid. These attacks can cause significant financial losses due to business downtime, lost productivity, and the potential ransom payment itself. Even seemingly minor cyberattacks, such as phishing scams that target employees, can incur costs associated with data recovery, employee training, and lost productivity.
According to a 2023 report by IBM Security, the average cost of a data breach for organizations in the Middle East reached a staggering SAR 29.9 million (approximately $8 million USD). This alarming statistic highlights the severe financial consequences businesses in the UAE can face if they fail to prioritize cybersecurity measures.
What is a Cybersecurity Risk Assessment?

A cybersecurity risk assessment is a systematic process that identifies, analyzes, and prioritizes potential threats to your organization’s IT infrastructure and data security. It acts as a security gap analysis, meticulously examining your systems and practices to uncover vulnerabilities that cybercriminals could exploit. By proactively understanding your risk landscape, you can take necessary steps to mitigate these vulnerabilities and minimize the potential financial and reputational damage from a cyberattack.
Risk assessments come in various scopes, tailored to your specific needs. A high-level assessment provides a broad overview of your security posture, while a detailed assessment delves deeper into specific systems and applications. The chosen approach hinges on factors like the size and complexity of your business, as well as the types of data you handle.
Regardless of the chosen scope, the typical risk assessment process follows a structured approach:
- Define the Scope: Clearly identify the IT assets and data included in the assessment.
- Identify Threats and Vulnerabilities: Pinpoint potential threats like malware attacks or phishing attempts, and identify any weaknesses in your systems or practices that could be exploited.
- Analyze Risks: Evaluate the likelihood of each threat occurring and the potential impact on your business if it does.
- Prioritize Risks: Rank the identified risks based on the combined likelihood and potential impact.
- Develop Mitigation Strategies: Formulate strategies to address the identified risks, aiming to reduce their likelihood or impact. This may involve implementing security controls, employee training, or policy changes.
By conducting a cybersecurity risk assessment, businesses gain an invaluable understanding of their security posture and can make informed decisions about resource allocation for cybersecurity measures. This proactive approach is crucial for safeguarding your business from cyberattacks and minimizing the potential financial losses they can inflict.
Benefits of Conducting a Cybersecurity Risk Assessment

In the ever-evolving cybersecurity landscape, conducting a cybersecurity risk assessment offers a multitude of benefits for businesses in the UAE. It acts as a comprehensive vulnerability assessment, meticulously examining your IT infrastructure and data security practices to expose potential weaknesses. By proactively identifying these vulnerabilities, businesses can take crucial steps to fortify their defenses and significantly reduce the risk of cyberattacks.
One of the primary benefits of a risk assessment is the ability to prioritize and optimize resource allocation for cybersecurity. Imagine navigating a vast, uncharted territory – without a map, it’s difficult to identify and address potential hazards. A risk assessment functions as that map, providing a clear picture of your security posture by highlighting the most critical vulnerabilities. This enables businesses to focus their cybersecurity efforts on the areas that pose the greatest risk, ensuring a more efficient allocation of resources.
Furthermore, risk assessments play a vital role in ensuring compliance with data privacy regulations like the UAE’s Data Protection Law. This law mandates that businesses implement appropriate technical and organizational measures to protect personal data. A risk assessment helps identify areas where your data security practices may fall short of these regulations, allowing you to take corrective actions and demonstrate compliance with the authorities.
Beyond regulatory compliance, risk assessments contribute to building a robust data security culture within your organization. By fostering an awareness of potential cyber threats and vulnerabilities, employees become more vigilant and can better identify and report suspicious activity. This collective vigilance forms a powerful line of defense against cyberattacks.
Ultimately, a cybersecurity risk assessment provides businesses with a clear understanding of their risk landscape, enabling them to make informed decisions about their cybersecurity strategy. By proactively addressing vulnerabilities and prioritizing resources effectively, businesses can significantly reduce the financial and reputational damage caused by cyberattacks, ensuring a more secure and prosperous future.
How to Conduct a Cybersecurity Risk Assessment
Conducting a cybersecurity risk assessment can be approached in two ways: internal or external. An internal assessment, led by your own IT team, provides a cost-effective option but may lack the objectivity of an external assessment. External assessments, conducted by qualified cybersecurity professionals, offer a more comprehensive and unbiased perspective but come at a higher cost.
The key steps involved in a cybersecurity risk assessment process follow a logical flow:
- Define the Scope: Clearly outline the assets and data included in the assessment. This might encompass your network infrastructure, servers, desktops, laptops, mobile devices, applications, and any sensitive data you store.
- Identify and Classify Assets: Create a comprehensive inventory of your IT assets, categorizing them based on their criticality and the type of data they store. This prioritization helps focus efforts on the most valuable assets.
- Analyze Threats and Vulnerabilities: Meticulously examine your systems and practices to identify potential security gaps that cybercriminals could exploit. This involves understanding common cyber threats relevant to your industry, such as malware attacks, phishing attempts, or data breaches.
- Evaluate Risks: For each identified vulnerability, assess the likelihood of it being exploited (threat) and the potential impact on your business if a cyberattack occurs. Factors to consider for impact include financial losses, reputational damage, and operational disruption.
- Prioritize Risks: Combine the likelihood and impact scores to determine a risk score for each vulnerability. High-risk vulnerabilities with a high likelihood of occurrence and severe potential impact require immediate attention.
- Develop and Implement Mitigation Strategies: Formulate a plan to address the identified vulnerabilities. This may involve patching software, implementing additional security controls (e.g., firewalls, intrusion detection systems), or revising data security policies and employee training programs.
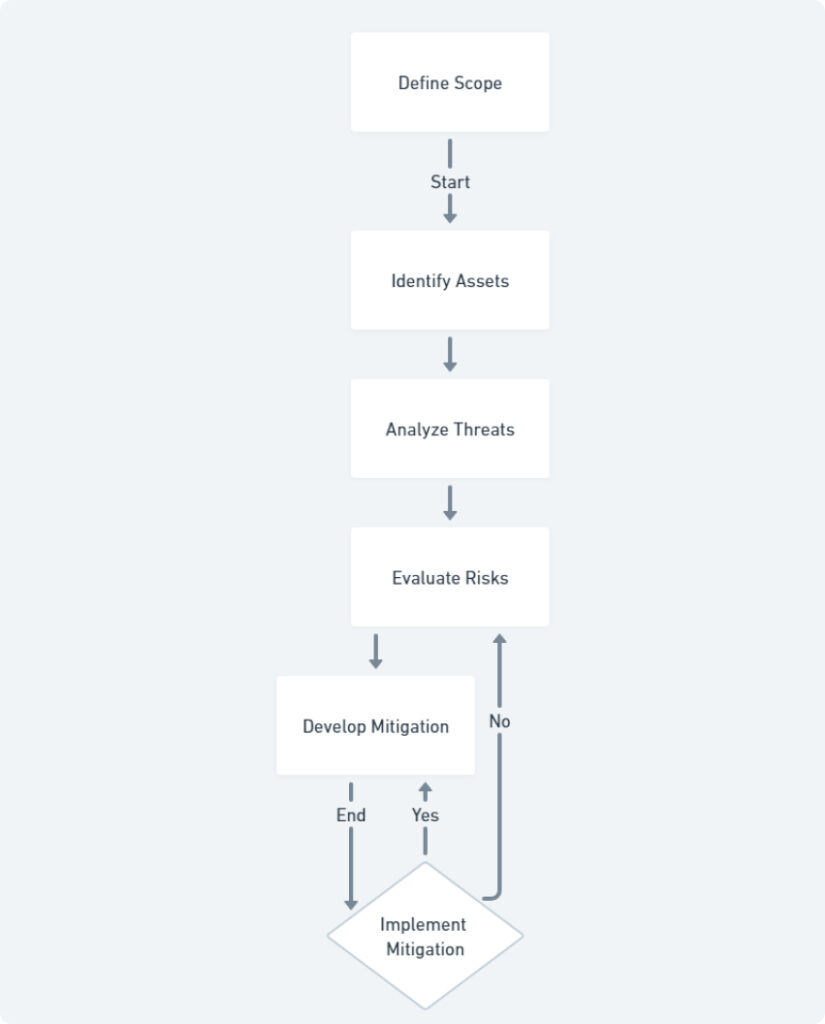
By following these steps and choosing the approach that best suits your needs, businesses can conduct a comprehensive cybersecurity risk assessment. This proactive approach empowers them to identify and address vulnerabilities, ultimately minimizing the risk of cyberattacks and safeguarding their valuable data and operations.
Best Practices for Cybersecurity Risk Assessments in the UAE

For businesses operating in the UAE, conducting a cybersecurity risk assessment is not just a best practice – it’s a necessity. The UAE enforces a unique regulatory landscape with data privacy regulations like the Data Protection Law. A well-designed risk assessment can ensure your security practices align with these regulations, minimizing the risk of hefty fines for non-compliance.
To maximize the effectiveness of your risk assessment, consider these key practices:
- Involve Relevant Stakeholders: Don’t conduct the assessment in a silo. Include representatives from various departments, such as IT, legal, and human resources. Their insights will provide a holistic understanding of your security posture and potential vulnerabilities across different functions.
- Regular Assessments are Key: The cybersecurity threat landscape is constantly evolving. Don’t settle for a one-time assessment. Schedule regular assessments, at least annually, to identify new threats and ensure your mitigation strategies remain effective.
- Seek Expert Guidance: While internal assessments offer a cost-effective option, complex environments may benefit from the expertise of qualified cybersecurity professionals. Their experience with advanced threats and mitigation strategies can significantly enhance the assessment’s effectiveness.
- Leverage UAE Government Resources: The UAE government prioritizes cybersecurity and offers valuable resources for businesses. The Dubai Cyber Security Council provides a wealth of information, including best practices for conducting risk assessments in the UAE context.
By following these best practices, UAE businesses can ensure their cybersecurity risk assessments are comprehensive, compliant, and effective. This proactive approach minimizes the risk of cyberattacks and empowers them to thrive in the ever-growing digital landscape of the UAE.
Safeguarding Your Digital Future Through Proactive Risk Management
In the dynamic digital landscape of the UAE, cybersecurity threats pose a significant risk to businesses of all sizes. The financial consequences of cyberattacks can be devastating, leading to data breaches, reputational damage, and operational disruption. A cybersecurity risk assessment emerges as a powerful tool for mitigating these risks and safeguarding your financial well-being.
By proactively identifying vulnerabilities within your IT infrastructure and data security practices, a risk assessment empowers you to prioritize resources and implement effective security controls. This proactive approach significantly reduces the likelihood of a successful cyberattack, preventing the financial losses associated with data breaches, downtime, and potential regulatory fines.
The benefits of conducting a cybersecurity risk assessment are undeniable. Don’t wait for a cyberattack to expose your vulnerabilities. Take action today and implement a risk assessment strategy to safeguard your business and ensure a secure future in the digital age.
For a deeper dive into integrating cloud security with traditional cybersecurity approaches, explore our companion article.
For expert guidance on conducting a comprehensive cybersecurity risk assessment tailored to your specific needs in the UAE, consider consulting with Cybernod, a leading provider of cybersecurity solutions. Our team of qualified professionals can help you identify and address your vulnerabilities, ensuring your business remains resilient in the face of ever-evolving cyber threats.
Categorized in:
Comments