
In an era of increasing cyber threats, protecting business identity is more critical than ever, especially as digital networks expand globally. For small and medium-sized businesses in the UAE, the risk of having sensitive information exposed is heightened by the growing sophistication of cybercriminals. Reports indicate that over 60% of data breaches involve compromised credentials, making businesses vulnerable to financial losses, reputational damage, and legal implications.
Dark web monitoring has emerged as a crucial tool in this defense strategy, allowing businesses to detect stolen data being sold or traded on underground platforms. By identifying risks before they escalate into full-blown security incidents, businesses can take proactive measures to safeguard their assets. For UAE companies, the importance of staying ahead of these threats cannot be overstated, especially in an environment where data is an invaluable asset.
What is the Dark Web?
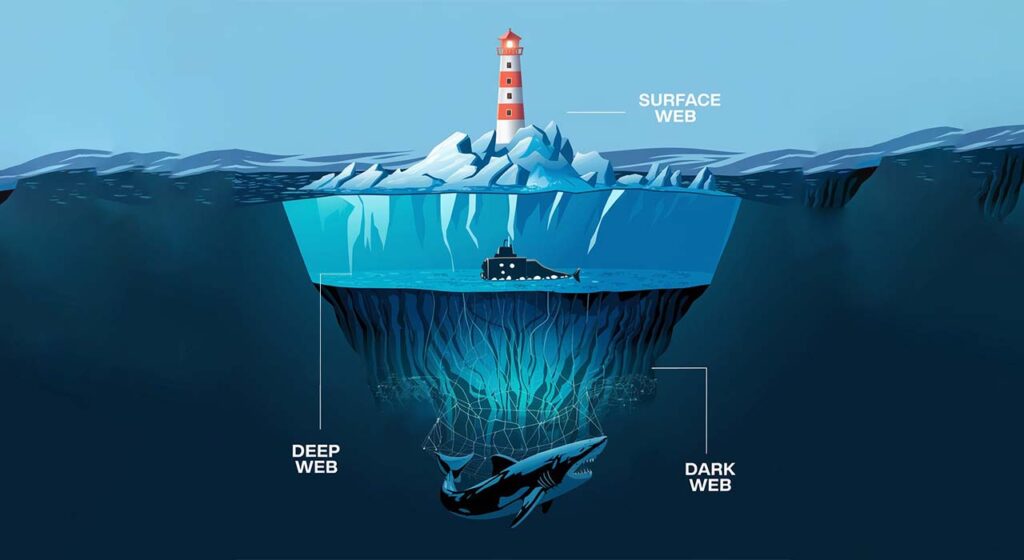
The internet is divided into three main layers: the surface web, deep web, and dark web. The surface web consists of publicly accessible websites that search engines can index, such as business websites, blogs, and social media platforms. Beneath this lies the deep web, which includes databases, internal networks, and other content not indexed by search engines. While most of the deep web is harmless and often used for private or academic purposes, the dark web represents a more dangerous and hidden layer.
Accessible only through specific software such as Tor, the dark web is a breeding ground for illicit activities, including the sale of stolen data, illegal drugs, and counterfeit goods. Cybercriminals exploit this space to sell sensitive business information, including employee credentials, intellectual property, and customer data. These illegal transactions expose businesses to significant cybersecurity risks that often go unnoticed without proper monitoring. Europol’s Internet Organised Crime Threat Assessment (IOCTA) highlights how the dark web facilitates cybercrime by enabling the sale of stolen data and hacking tools, further illustrating the necessity of cybersecurity risk assessment for businesses .
How Does the Dark Web Endanger Your Business Identity?
The dark web poses significant risks to businesses, particularly in regions like the UAE, where cybersecurity breaches can lead to severe financial and reputational damage. One of the top cybersecurity threats for small businesses is the exposure of stolen credentials. Once compromised, employee login details, admin passwords, and other sensitive access points can be sold on dark web marketplaces. According to a report from Symantec, over 80% of breaches involve weak or stolen credentials, which makes businesses prime targets for cybercriminals looking to exploit security gaps.
The dark web poses significant risks to businesses, particularly in regions like the UAE, where cybersecurity breaches can lead to severe financial and reputational damage. One of the top cybersecurity threats for small businesses is the exposure of stolen credentials. Once compromised, employee login details, admin passwords, and other sensitive access points can be sold on dark web marketplaces. According to a report from Symantec, over 80% of breaches involve weak or stolen credentials, which makes businesses prime targets for cybercriminals looking to exploit security gaps.
Intellectual property theft is another threat that can be equally devastating. Trade secrets, proprietary algorithms, and product designs may end up in the hands of competitors or malicious actors, causing long-term harm. For example, Verizon’s Data Breach Investigations Report indicates that small businesses face increasing threats to their intellectual property as cybercriminals seek high-value targets on the dark web.
The Role of Dark Web Monitoring in Protecting Business Identity

Dark web monitoring plays a vital role in protecting a business’s identity by providing early detection of potential threats. This service continuously scans dark web forums, marketplaces, and encrypted websites for any mention of a company’s sensitive data, such as stolen credentials, intellectual property, or customer information. The value of dark web monitoring lies in its proactive approach alerting businesses before their data is exploited, rather than reacting after a breach has occurred.
For UAE businesses, the need for dark web monitoring is especially critical due to the region’s growing digital economy and the increasing sophistication of cybercriminals. A comprehensive security gap assessment that includes dark web monitoring can reveal vulnerabilities that traditional cybersecurity measures may overlook. Many breaches start with stolen credentials, which are often traded on the dark web. Detecting these compromised credentials early can help businesses take preventive action, such as resetting passwords or implementing multi-factor authentication, before attackers use them to access internal systems.
The best dark web monitoring tools provide more than just passive scanning; they offer real-time alerts, detailed reports, and recommendations for closing security gaps. Platforms like CyberNod provide businesses with tailored monitoring services, alerting them to potential threats and offering remediation strategies. According to a success story from Recorded Future, one company was able to prevent a major breach by identifying compromised employee credentials on the dark web before they were used maliciously.
| Feature | Proactive Monitoring | Reactive Monitoring |
|---|---|---|
| Threat Detection | Real-time scanning of dark web for compromised data, early detection of potential threats | Identifies threats after they have caused a breach or incident |
| Alert Systems | Instant alerts to notify businesses of detected threats or exposed data | Alerts triggered only after a breach has been identified |
| Reporting Mechanisms | Comprehensive, continuous reports that allow businesses to assess risks and take preventive actions | Post-incident reports that analyze breaches after they have occurred |
| Data Protection | Helps prevent the exploitation of stolen credentials or intellectual property before any damage is done | Only mitigates damage after sensitive data has been compromised |
| Response Time | Immediate action can be taken to secure compromised assets and prevent breaches | Delayed response, action is taken only after the breach is detected |
| Vulnerability Assessment | Ongoing assessment of security gaps through real-time intelligence, including gap analysis | Vulnerabilities are often discovered too late, typically during post-breach investigations |
| Cost Effectiveness | Reduces long-term costs by preventing incidents before they escalate | Higher costs related to post-incident damage control and recovery |
The Benefits of Dark Web Monitoring for UAE Businesses
Dark web monitoring offers several critical benefits for businesses in the UAE, particularly in the realm of cybersecurity services for small businesses. One of the most important advantages is early detection of threats. By continuously scanning dark web forums and marketplaces for compromised data, businesses can identify potential breaches before they cause damage. This proactive approach significantly reduces the risk of data exposure, allowing companies to respond quickly and mitigate threats, rather than reacting after a breach has already occurred.
Additionally, dark web monitoring provides substantial cost savings. The cost of recovering from a data breach can be astronomical, especially for small businesses. According to a report by IBM, the average cost of a data breach in the Middle East is around $6 million. By investing in proactive measures like dark web monitoring, businesses can avoid these costly aftermaths. A study from Deloitte emphasizes the ROI of proactive cybersecurity, showing that for every dollar invested in early threat detection, businesses can save up to $9 in breach recovery costs.
Another crucial benefit of dark web monitoring is compliance with cybersecurity regulations. In the UAE, businesses must adhere to strict data protection laws, particularly with regard to handling sensitive customer information. Failure to comply with these regulations can result in heavy penalties and damage to a company’s reputation. Dark web monitoring helps small businesses ensure they are in compliance with these standards by detecting any potential leaks of regulated data early on, giving them time to take appropriate measures.
Incorporating dark web monitoring into a broader cybersecurity strategy enables UAE businesses to stay ahead of evolving threats, save on breach-related costs, and ensure they comply with local and international cybersecurity regulations.
How Dark Web Monitoring Saved a UAE Business
In 2021, Kaspersky helped a global logistics company prevent a major data breach through dark web monitoring. The company, with operations in the UAE, had implemented Kaspersky’s dark web monitoring service as part of their cybersecurity strategy. The system detected the presence of employee login credentials on a dark web marketplace, alerting the company before these credentials could be exploited.
Upon receiving the alert, the company acted swiftly, resetting the compromised accounts and implementing stronger authentication measures. This early detection not only prevented a significant breach but also saved the company from potential financial and reputational harm. The cost of recovering from such a breach could have been severe, especially in the logistics industry, where operational downtime can lead to substantial losses. This case illustrates how dark web monitoring can help prevent data breaches for small businesses and maintain compliance with UAE’s cybersecurity regulations.
How to Get Started with Dark Web Monitoring
To implement dark web monitoring for your business, follow a structured approach that ensures maximum protection from potential threats. The first step is to choose the best cybersecurity solution tailored to your specific needs. Look for trusted providers that offer comprehensive dark web monitoring, such as CyberNod, which specializes in proactive threat detection and real-time alerts. Their services include monitoring compromised credentials, intellectual property, and sensitive business data across various dark web forums and marketplaces.
Once you’ve selected a provider, it’s essential to conduct a thorough cybersecurity assessment. This assessment will identify your current vulnerabilities and help the provider customize monitoring services to cover your high-risk areas. Regular updates and reports should also be part of your monitoring routine to ensure continuous protection.
In addition to professional services, businesses can also take advantage of free cybersecurity resources available online to stay informed and improve their overall defense. These resources can guide small businesses through best practices, regulations, and the latest cybersecurity trends. By combining professional monitoring with accessible resources, businesses can take an effective and proactive approach to safeguarding their information.
For trusted dark web monitoring services, consider visiting CyberNod’s website to explore how their tailored solutions can help your business stay secure.
The Future of Business Security in the UAE

As UAE businesses face increasingly sophisticated cyber threats, integrating dark web monitoring into a comprehensive cybersecurity strategy is no longer optional. By proactively identifying stolen data and potential breaches before they escalate, businesses can protect their sensitive information and maintain a strong security posture. For small businesses, in particular, adopting dark web monitoring can prevent devastating financial and reputational losses while ensuring compliance with evolving data protection regulations.
As UAE businesses face increasingly sophisticated cyber threats, integrating dark web monitoring into a comprehensiveIncorporating regular cybersecurity risk assessments and leveraging dark web monitoring not only addresses immediate threats but also strengthens long-term resilience. The future of business security in the UAE will depend on the ability of organizations to stay ahead of these threats by utilizing advanced monitoring solutions and maintaining vigilance across all areas of cybersecurity. cybersecurity strategy is no longer optional. By proactively identifying stolen data and potential breaches before they escalate, businesses can protect their sensitive information and maintain a strong security posture. For small businesses, in particular, adopting dark web monitoring can prevent devastating financial and reputational losses while ensuring compliance with evolving data protection regulations.
For a more in-depth exploration of cybersecurity strategies and technologies, we recommend reading our comprehensive guide, ‘Creating a Scalable Cybersecurity Strategy with Cloud and AI Technologies.’ This article delves into the latest trends and best practices for protecting your business in the UAE’s digital landscape.”
Categorized in:
Comments