
The dark web represents a concealed layer of the internet that is inaccessible through conventional search engines. While it accounts for a relatively small portion of online activity, its significance is disproportionate to its size. Studies estimate that only 0.01% of websites globally are accessible via the dark web, yet these platforms host a disproportionate volume of illicit activities. For example, data breaches often result in stolen credentials being sold on dark web marketplaces, with 64% of organisations worldwide admitting they have been impacted by data traded in this hidden network.
Beyond its association with cybercrime, the dark web has also become a refuge for whistleblowers, journalists, and individuals in oppressive regimes seeking privacy or secure communication channels. This duality—a haven for anonymity yet a hub for illicit trade—makes the dark web both a vital tool and a significant threat, sparking global conversations about cybersecurity and digital ethics.
Understanding the Layers of the Internet
The internet is commonly divided into three distinct layers: the surface web, deep web, and dark web. Each layer serves different purposes and has unique characteristics that contribute to the overall functionality of the online ecosystem.
The surface web is the most familiar layer, comprising websites indexed by search engines like Google or Bing. This layer includes publicly accessible platforms such as news websites, e-commerce stores, and social media. It represents only about 4% of the entire internet.
The deep web is significantly larger, accounting for approximately 90–95% of online content. Unlike the surface web, it consists of pages not indexed by standard search engines. Examples include password-protected databases, academic research repositories, and private corporate networks. These are legitimate resources that remain hidden for reasons such as privacy or security.
The dark web represents a much smaller segment of the deep web, accessible only through specialized tools like the Tor browser. Unlike the deep web, which hosts primarily lawful content, the dark web is notorious for enabling anonymous activities, including illegal trade and the sale of stolen data. However, it also supports privacy-focused activities, such as encrypted communication for journalists and activists in restrictive environments.
What Is the Dark Web?

The dark web refers to a concealed part of the internet that cannot be accessed through standard web browsers like Chrome or Safari. Instead, it requires specialized software such as the Tor browser, which anonymizes user activity by routing traffic through multiple encrypted nodes. This layer of the internet is purpose-built to provide privacy, ensuring users can browse or host websites without revealing their identities or locations.
Contrary to common belief, the dark web is not inherently illegal. It hosts a mix of lawful and unlawful activities. For instance, journalists and whistleblowers in restrictive regimes often rely on the dark web for secure communication. On the other hand, it is also infamous for enabling illegal trade, including the sale of stolen data, counterfeit documents, and illicit substances.
A critical distinction lies between the dark web and the deep web. While the deep web includes legitimate, unindexed content such as private databases and subscription-only platforms, the dark web specifically facilitates anonymity. This feature has given rise to misconceptions, such as the assumption that all dark web activities are criminal, overshadowing its legitimate uses.
Accessing the dark web is neither inherently illegal nor unethical, but it comes with risks. Cybersecurity vulnerabilities, exposure to illegal content, and potential surveillance are significant concerns for users. Businesses should consider cybersecurity risk assessment and security gap analysis to safeguard sensitive information from being traded on the dark web.
Resource: For an in-depth explanation, visit CSO Online’s guide.
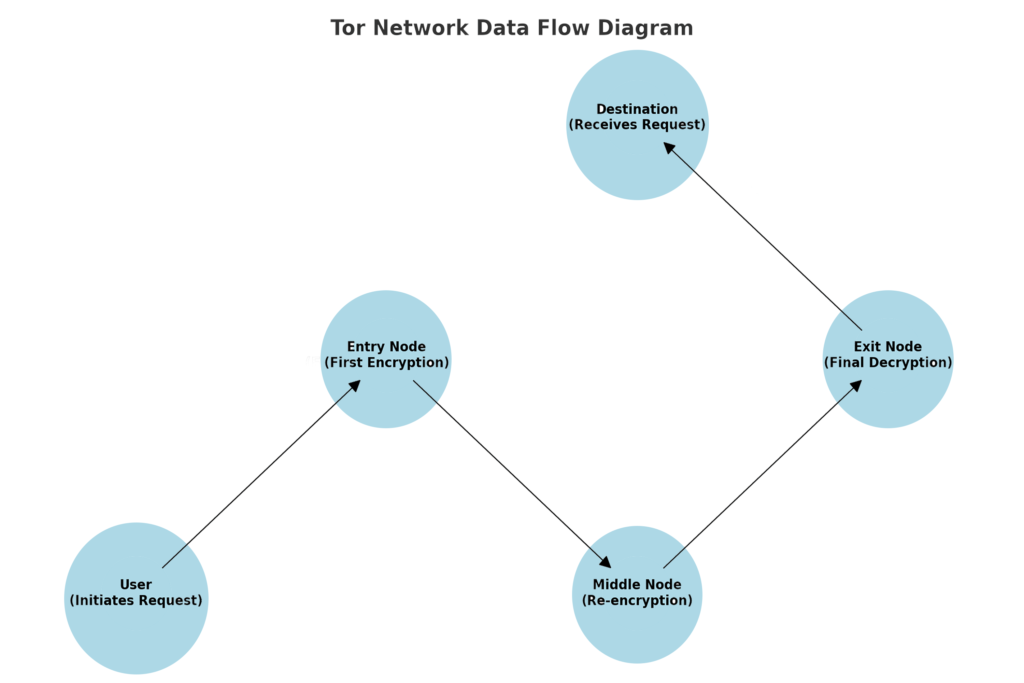
How Does the Dark Web Work?
The dark web functions through a combination of advanced technologies designed to ensure anonymity for users and websites. The most widely used tool for accessing the dark web is the Tor (The Onion Router) network, which uses a method called onion routing to obscure user identities and activities.
Onion routing encrypts data multiple times before sending it through a series of volunteer-operated servers, called nodes or relays. Each node decrypts one layer of encryption and passes the partially decrypted data to the next node. This procedure proceeds until the final node, referred to as the exit node, removes the final layer of encryption and transmits the request to its intended destination. At no point do any of the nodes know both the origin and destination of the data, ensuring user anonymity.
The Tor network is accessed using the Tor browser, which is freely available and configured to connect to onion sites (.onion domains). Unlike traditional browsers, the Tor browser does not track user activities, block ads, or store cookies, making it a critical tool for accessing dark web content securely. However, it’s important to note that anonymity does not equate to complete security. Users remain vulnerable to cybersecurity threats like malware and phishing attacks if they engage in unsafe practices.
The dark web’s infrastructure allows users to bypass censorship and maintain privacy, which has legitimate uses, such as secure communications for whistleblowers. However, the same anonymity also facilitates illegal activities, including data breaches and unauthorized sales. Businesses are encouraged to conduct regular cybersecurity risk assessments to prevent their data from being traded on the dark web.
Why Does the Dark Web Exist?

The dark web exists to address both legitimate and illegitimate needs in the digital landscape. Its core purpose lies in enabling anonymity and privacy, making it a crucial tool for various activities, from safeguarding personal freedoms to facilitating criminal enterprises.
On the legitimate side, the dark web provides a platform for whistleblowers, journalists, and activists operating under oppressive regimes. For instance, platforms like SecureDrop allow individuals to anonymously share sensitive information with news organizations, bypassing censorship and surveillance. Similarly, the dark web serves as a haven for privacy-conscious users who wish to keep their online activities shielded from pervasive tracking and data collection.
The dual nature of the dark web underscores its complexity. While it empowers individuals to uphold freedom of expression and privacy, it simultaneously harbors activities that compromise security. For businesses, this duality highlights the importance of conducting regular cybersecurity assessments and implementing robust measures to prevent sensitive data from being exposed or traded on the dark web.
Risks and Challenges Associated with the Dark Web
Accessing the dark web presents significant risks and challenges, even for well-informed users. While it offers anonymity and privacy, these benefits come with considerable dangers, including exposure to illegal content, cybersecurity threats, and potential legal consequences.
One of the most concerning aspects of the dark web is the prevalence of illegal activities. Users may inadvertently encounter illicit content, such as child exploitation materials, counterfeit documents, or illegal drug marketplaces. Even browsing such content, intentionally or not, can have severe legal ramifications in many jurisdictions.
From a cybersecurity perspective, the dark web is rife with risks. Many websites on the dark web contain malicious links or host malware designed to compromise user systems. Phishing attacks are also prevalent, exploiting the anonymity of the environment to steal credentials or financial information. Individuals without robust cybersecurity measures, such as VPNs, firewalls, and updated antivirus software, are particularly vulnerable.
Legal implications further complicate dark web use. While accessing the dark web itself is not illegal in most countries, engaging with illicit activities or even visiting suspicious websites can attract the attention of law enforcement agencies.
For businesses, the dark web represents a critical security threat. Stolen credentials, trade secrets, and personal customer information are frequently sold on dark web marketplaces. Conducting regular cybersecurity assessments and implementing security gap analyses are essential measures to protect sensitive data.
The Dark Web's Impact on Cybersecurity

The dark web significantly influences the cybersecurity landscape, acting as a hub for cybercriminals to exploit vulnerabilities and trade illicit goods. One of its most concerning impacts is the sale of stolen data, including personal information, financial credentials, and intellectual property. High-profile data breaches often lead to such information being listed on dark web marketplaces, where it can be sold to the highest bidder.
Beyond the sale of stolen data, the dark web facilitates the proliferation of cyber threats. Tools for hacking, malware, and ransomware are readily available for purchase, lowering the barrier for cybercriminals to launch sophisticated attacks. Forums on the dark web also provide spaces for malicious actors to exchange knowledge, collaborate, and refine their techniques.
For organizations, this presents a critical security challenge. Cybersecurity risk assessments and regular monitoring of dark web activities are essential to identifying and mitigating threats before they result in significant damage.
Securing Your Digital Presence: Final Thoughts on the Dark Web
The dark web is a complex and multifaceted segment of the internet, serving both legitimate purposes, such as ensuring privacy and freedom of expression, and facilitating illicit activities like cybercrime and the sale of stolen data. Understanding its dual-use nature is essential for navigating its risks and leveraging its benefits responsibly. For businesses, proactive measures, including regular cybersecurity risk assessments and dark web monitoring, are vital to safeguarding sensitive information.
To strengthen your organization’s cybersecurity posture and protect against emerging threats, consider exploring our comprehensive dark web monitoring and security assessment services at Cybernod.
Categorized in:
Comments